Table of contents
- Welcome to the Future
- Beginner: Being Your Own Bank
- Intermediate: Navigating Web3
- Advanced: Reading Contracts, Audits and Revoking
- Conclusion
Welcome to the Future
So you've decided to dive into web3, dApps, and the fascinating world of degenerate gamblers and obstinate builders of the internet's future.
Or, perhaps you want to join in on the fun and experiment with new dApps, but are afraid of the numerous ways you see people losing money by falling for scams and malicious platforms. You're not tech savvy and believe you'll be an ideal victim for the next scam.
Fortunately for you, I'm sharing the fundamentals of online security when using crypto, DeFi, and web3.
This article will take you through the steps you should take in order to be safer as you learn and progress on web3. I'll assume you're using Google Chrome and Metamask, which are the most popular tools right now.
Beginner: Being Your Own Bank
The advantage of web3 logistics is that you set it once and don't have to worry about it again. You’ll gain confidence to go further in this new space if you secure your accounts and funds. So, let's start with the fundamentals and how to secure everything.
1. Enable Two-Factor Authentication on All Accounts
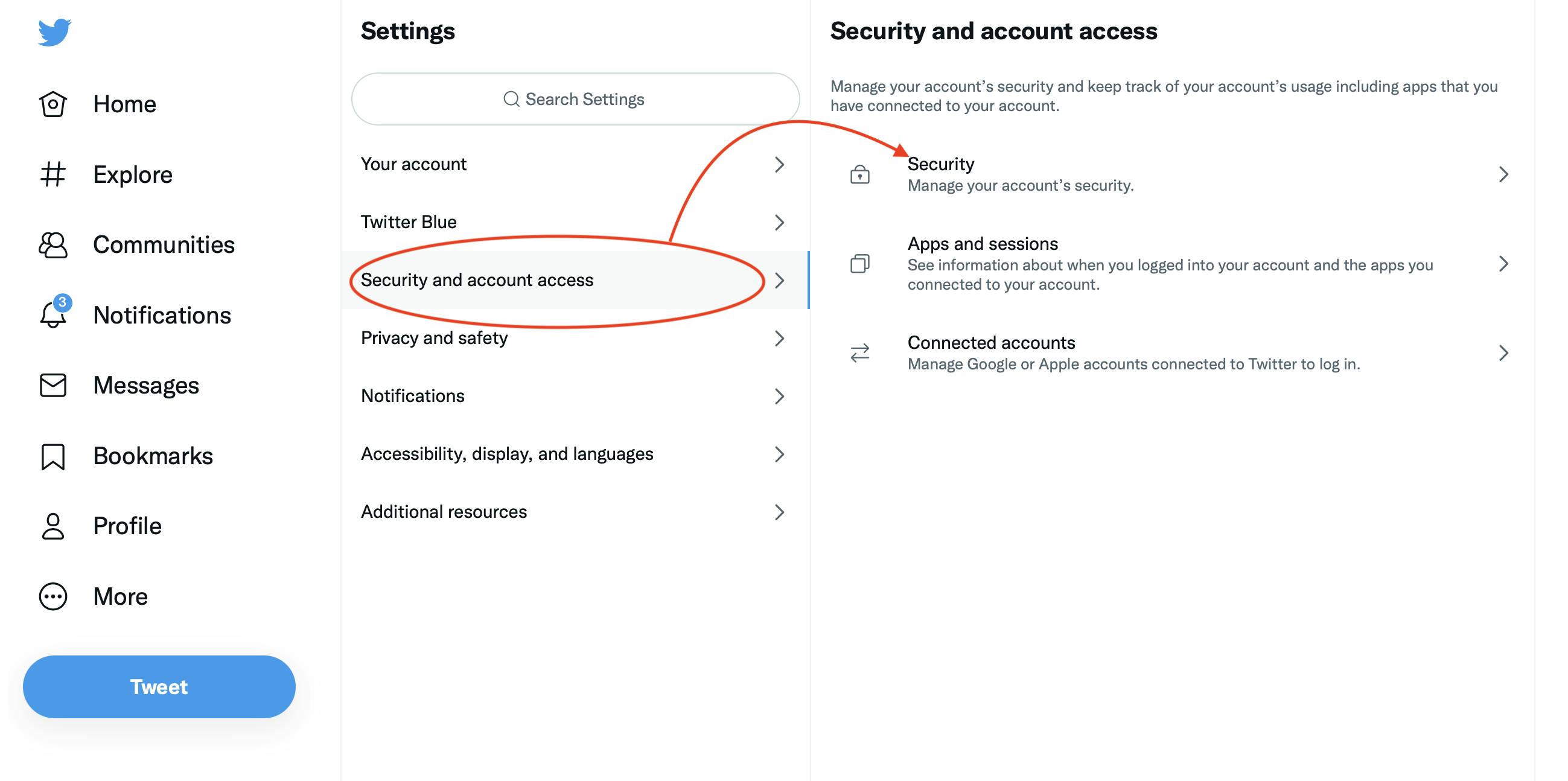
2FA, or Two Factor Authentication, will save you a lot of trouble if hacks occur on the centralized apps you use. When creating any account, go straight to settings and activate it. Here’s an example with a Twitter account, after going to “Settings”:
Step 1:
Step 2:
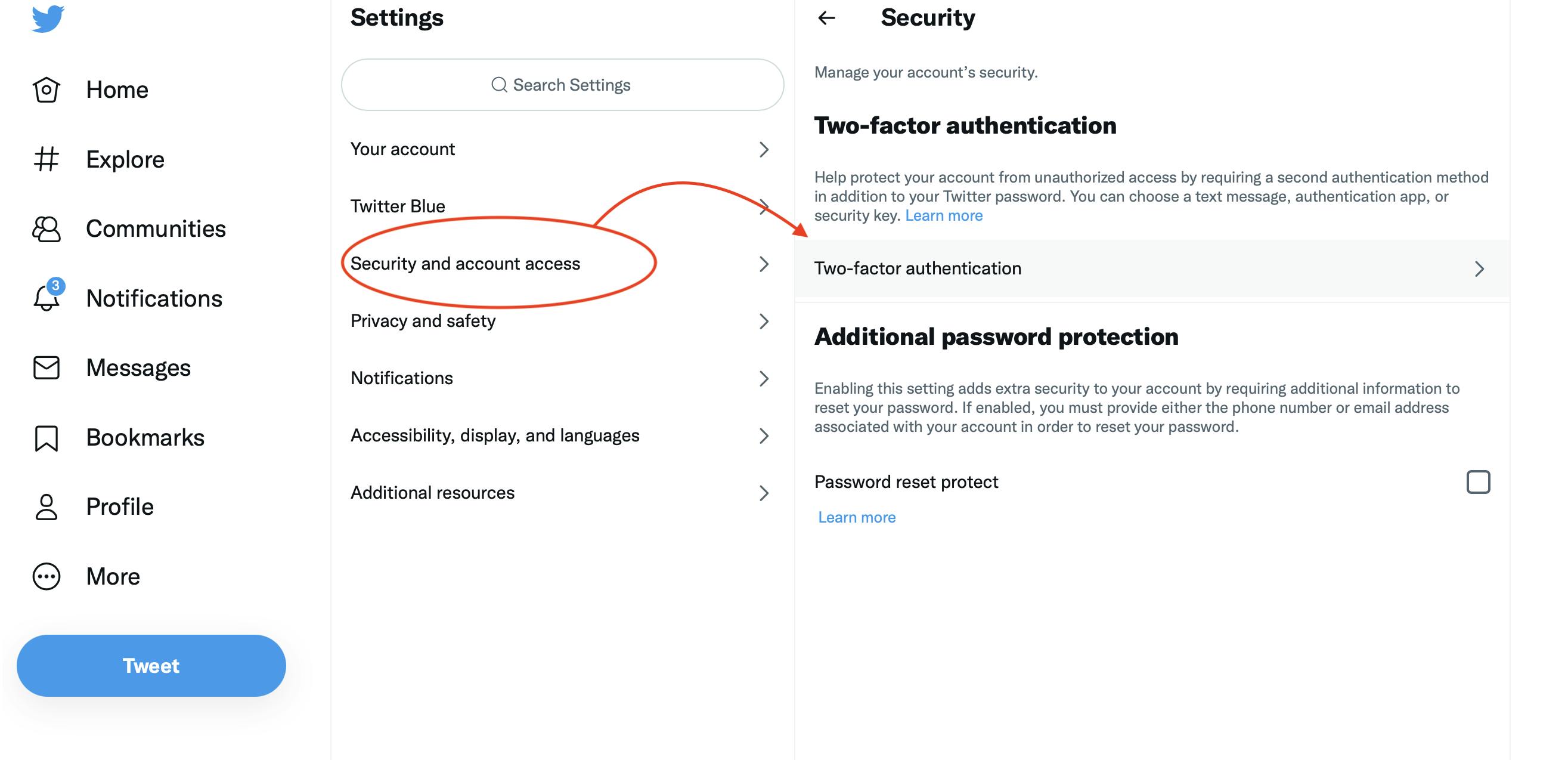
It’s critical that you don’t use a phone number as a 2FA measure, as SIM card swapping is a common practice among hackers nowadays. And yes, crypto users are also targeted.
Instead, you can use a 2FA app, which will generate a code for each time slot and allow you to log in after entering the code. The most popular 2FA apps are Google Authenticator and Authy.
Step 3:
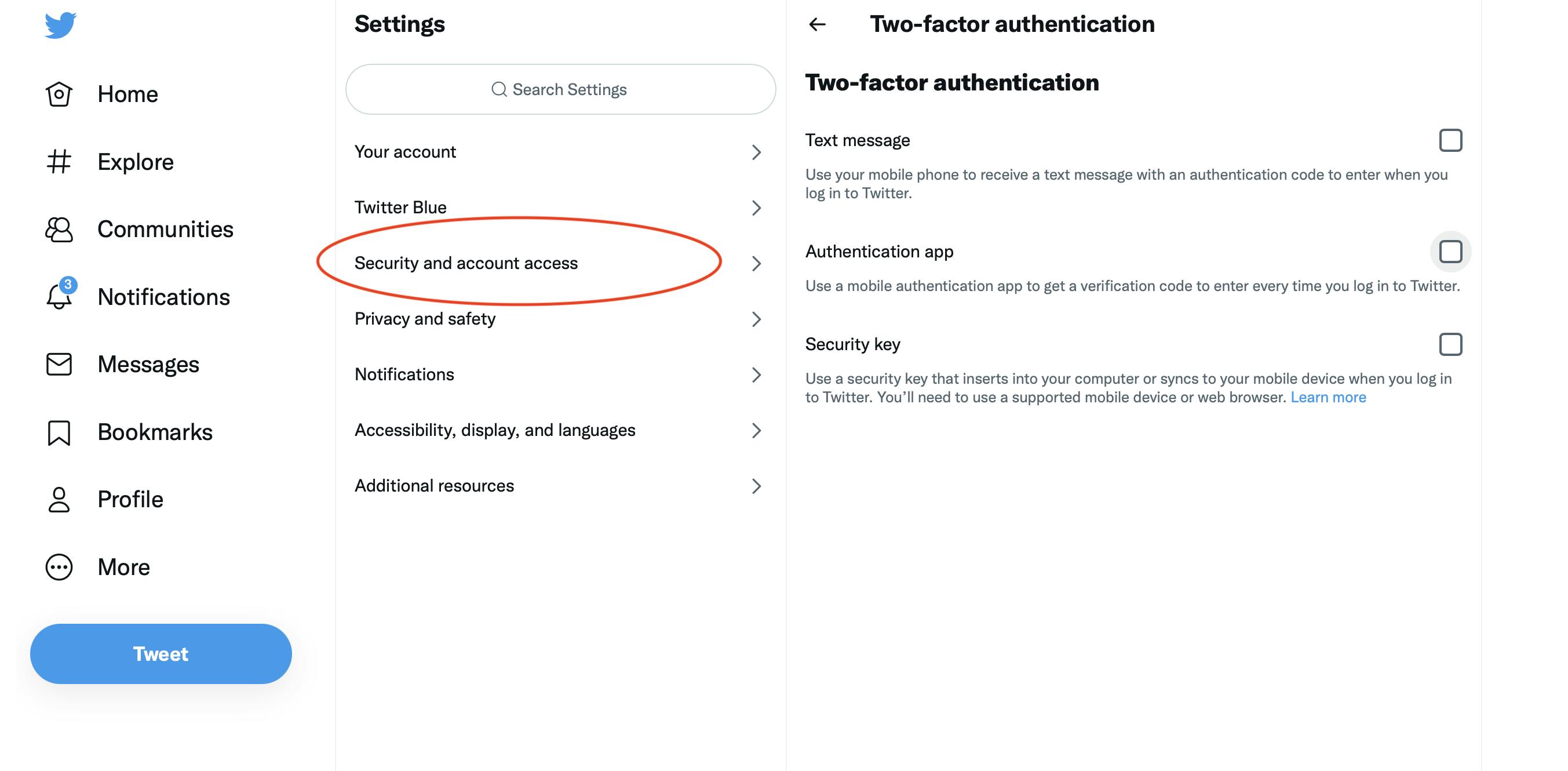
The first thing you should do is protect your CEX account, which is where you buy and sell crypto for fiat.
The next thing you should do is secure your social and forum accounts, where you discuss cryptocurrency, to avoid being hacked and granting access to potential victims, especially if you have a large audience.
Why Protect Your Social Accounts?
Having your social media accounts hacked can also disqualify you from projects in which you may be interested. For example, if your address is whitelisted to mint a project, the hacker can change it and replace it with his.
Hacked social media accounts can also be purchased for pennies on the internet. There’s a thriving market for verified Twitter accounts with large followings. Some specialized crypto websites will sell your rank on some servers (which usually grants you privileges such as airdrops, token allocations, or being on a private sale).
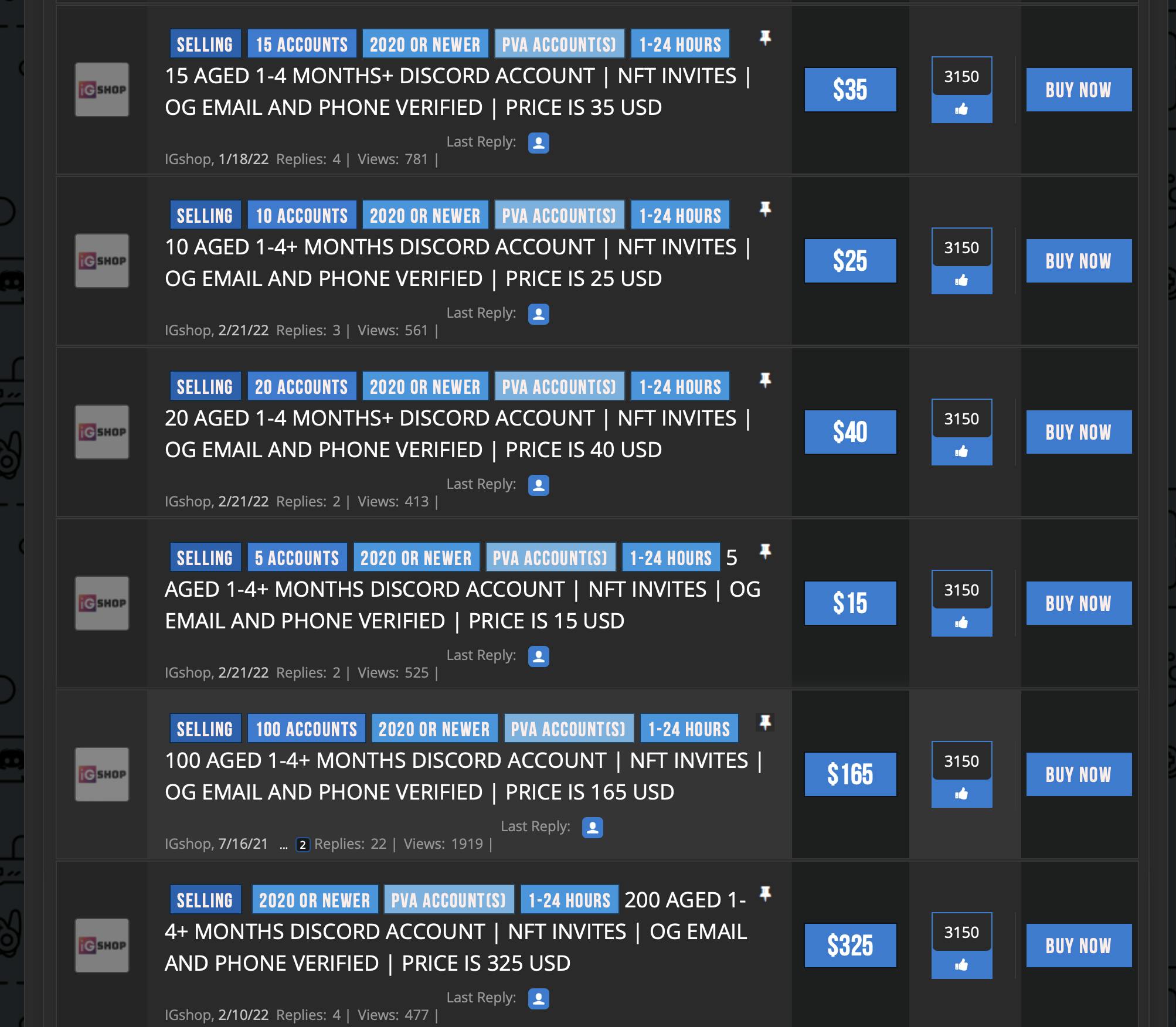
Typically, verified Twitter accounts are purchased by scammers or NFT projects with the intent of rug pulling (vanishing with people's coins after minting), or even cloning sites for successful projects. The scammers also need a fake account on a centralized exchange (CEX) to cash out the money.
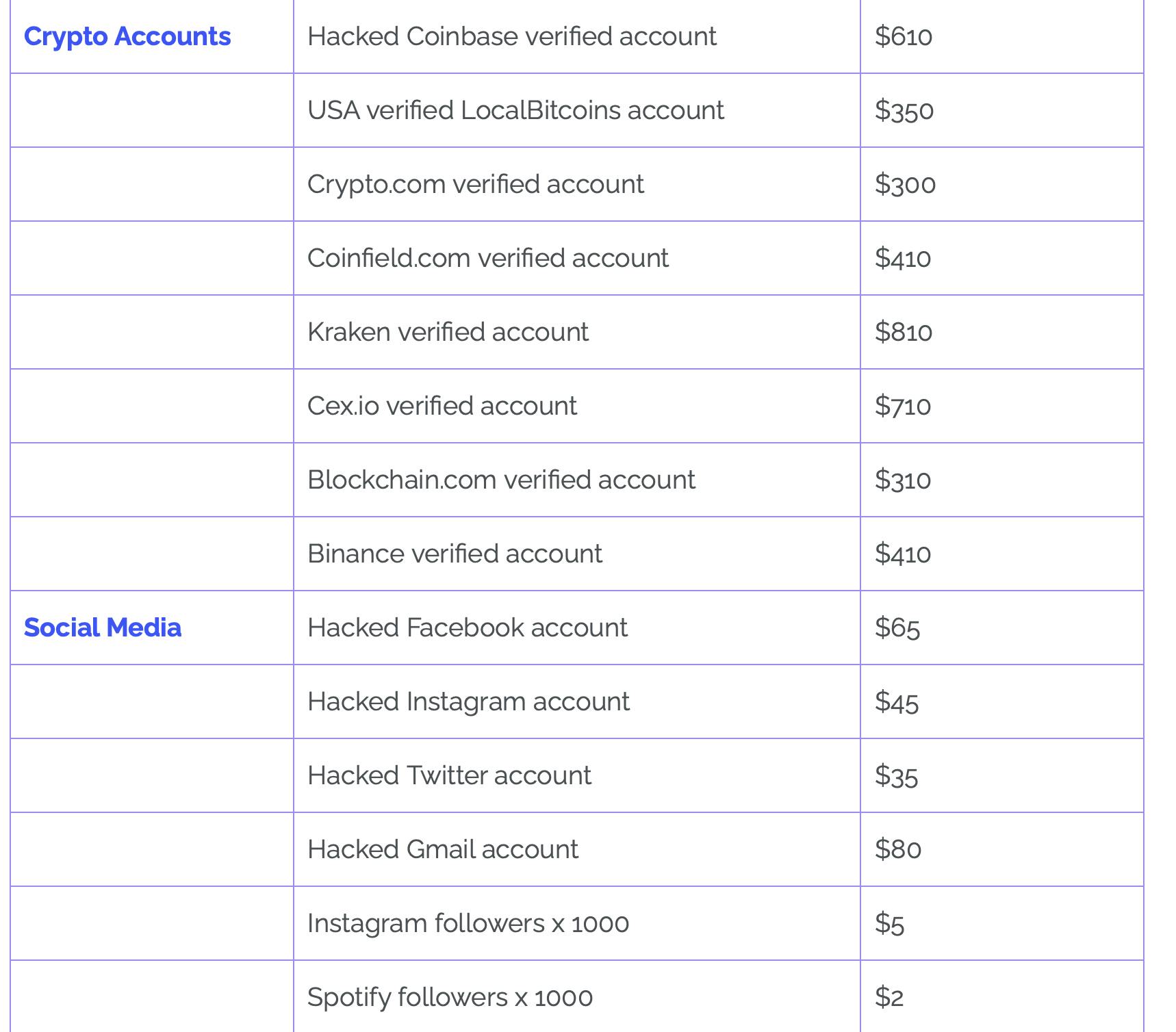
This screenshot is from this report. You can check it out if you want to learn more.
I've lost count of the number of times one of these hacked accounts has mentioned me on Twitter or added me to a fake giveaway list. People fall into the trap of associating being verified and having a large following with trust.
Scams Abound on Social Media
To avoid falling into this trap, keep this simple rule in mind: No one who has ever spoken to you will randomly give you anything or choose you to mint an exclusive project. No stranger with a large following will suddenly wake up, and decide to slide into your DMs to ask if "your trades are going smoothly."
Consider the social media platforms you use to discuss crypto at risk, even if you don't have a large following. Web3 identity and evolution are inextricably linked to web2 tools. When you realize how valuable they are, you'll want to protect them just as much as your coins.
2. Get a Hardware Wallet. Now.
Right now, Metamask is the most popular wallet, and it’s sometimes the only option for connecting to new projects and dApps. Setting up Metamask will most likely be your first step if you’re new to web3. Be wary of cloned extensions and make sure you're getting the real deal by visiting the official website.
Most people on web3 make the mistake of misinterpreting Metamask for a wallet, when it’s simply a browser extension that acts as an interface between dApps and your actual hardware wallet.
Whether you like the concept or not, a hardware wallet will be required at some point. Trezor and Ledger are the most popular hardware wallets, and they can be used in conjunction with Metamask as an additional layer. After you confirm an action on Metamask, you must confirm it physically by pressing the device. If you don’t physically press that button, no funds will be sent.
A Supplementary Protection Layer
Even if you connect to a malicious site, you'll be safe as long as you don't authorize anything with your hardware wallet. Without a hardware wallet, your Metamask could be hacked and start being remotely monitored by a hacker or a script.
Of course, these security layers will be useless if you sign on to a suspicious website that you have never seen before. But, don’t worry. We’re here to take you to the next level. But first, shall we secure that hardware wallet?
3. Mnemonic Phrase 101
A private key will be used to secure your cryptocurrency wallet. This private key is stored in your hardware wallet and tracks all of your actions. It’s usually a mnemonic phrase of 12 to 24 words.
This private key enables the user to restore any existing wallet on any device in the event that the physical wallet is lost or destroyed. In addition, they’re the weakest link in wallet management.
The secret key must be kept hidden at all times. You shouldn’t give it to anyone or post it on any website. Be wary of websites or users who request that you "resync" or "connect" your wallet by entering your private key. Your wallet will never need to be resynchronized. That is why blockchain technology exists.
Keeping Your Private Key Safe
Some cryptocurrency users have their wallets emptied without knowing how it happened. They never told anyone their phrase. Until they realize they're hosting it themselves...in the cloud or on their computer.
Your seed phrase must never be exposed to the internet, a keyboard, or any other electronic device that has previously been connected to the internet.
You shouldn’t take a screenshot of your seed phrase, print it, or store it anywhere, especially on your computer.
You should write it down, or at the very least, memorize it, and save it somewhere.
Keep in mind that anyone who finds this piece of paper will be able to recover your wallet and transfer your funds. Nobody should know where your seed phrase is stored, not even your wife.
If this piece of paper is destroyed for some reason, simply send your funds to a brand new wallet because relying solely on a device is, well, kind of risky.
4. Don't Click That Link, or Avoiding Phishing
Because you have a cryptocurrency wallet, you’ll most likely be targeted by phishing emails and links. If you receive an email advising you to download your crypto wallet's updated software as soon as possible, don't do so. First, check the brand's website, then their blog or social accounts to see if any updates have been announced.
To avoid phishing emails, a good piece of advice is to create a new email address that you’ll only use for crypto, and never click on any link sent to you, especially any attached files. NEVER.
Attached Files
Attached files in emails can contain malware that’ll hack your computer and attempt to steal your funds. Of course, if you use a hardware wallet, you have added an extra layer of security, but there are multiple exploits available that you’ll learn about on the medium and advanced levels.
As a general security precaution, don't open any attachments sent to you by an unknown email, and don't install anything with a .exe or .scr extension sent to you by a stranger.
Search Engines and Browsers
Another piece of advice is to avoid using Google as a search engine. If you use Google as a search engine, you'll find clones and phishing sites on the first page because scammers pay to rank on the first page. You can change the settings of any browser to use an alternative like DuckDuckGo or Ecosia.

Clone sites exist because the malicious actors behind them are aware that crypto users' funds are linked to a browser extension, which is technically vulnerable to hacking. Before DeFi went mainstream, there were clones of banks’ websites.
Compartmentalizing Your Online Activity
Using alternative search engines not only improves the accuracy of results, but also eliminates the majority of scam websites. The ultimate hack is to separate your activities: Use one browser for research and another for Metamask only.
Bookmark Links
Finding the official Twitter account for whatever dApp you're looking for (OpenSea, LooksRare, etc.) and bookmarking the link is common practice. This was the first thing I learned when I set up my Trezor for the first time.
Turn Off Private Messages on Discord
Turn off private messages if you're using Discord to follow some projects.
Scammers posing as administrators will ask for your seed phrase (a pretty obvious scam, but it still works) in order to "Connect your wallet," or will send you clone sites or phishing links. Some even call themselves "Announcements" to trick you into thinking they're a channel notification rather than a private message.
The Nice Bots Are Scammers
Do you have a problem with your wallet? Were you hacked? Did you fall victim to a scam and are now powerless? If you mention it in public, you might get the nice Metamask, Trust Wallet, or Coinbase support in your mentions or private messages offering to help. Don’t trust these accounts on social media.
Yes, once again, they’re scammers. I've seen people on Twitter talk about getting scammed, yet falling for another scam again. It's heartbreaking. So, let me state this once again: Your mother was correct, don't trust strangers on the internet.
Once your funds are depleted, they’re gone for good. There are some sophisticated ways to stop the draining; for example, if the hacker runs out of gas.
While there are white hat hackers who can eventually help you avoid an exploit in your wallet, the majority of people reaching out to you on social media to offer assistance are looking to take advantage of your desperation in such a situation.
Update Your Software
This should be standard practice for everyone, but it's especially important when entering web3. Hackers will take the shortest route by exploiting your software flaws. Updates include patches for vulnerabilities, as well as increased security.
Software flaws are everywhere, and the only way to detect them is after they’ve been exploited. As a result, if you receive a notification of a software update on the device in which you use a crypto-wallet, install it right away rather than wasting time worrying about how long it’ll take.
Frequent updates indicate that the team is aware of vulnerabilities and is working quickly to patch them. In the advanced level of this article, you’ll dig deeper into the Metamask code source to look for suspicious activity, but updating your software is one of the most effective ways to avoid being hacked and losing your coins and precious NFTs.
Intermediate: Navigating Web3
You’re all set once you’ve secured your funds, protected your social accounts, and ensured that they won't be wiped by a phishing link. It's time to move on to the next level of verification, where you'll learn how to verify the information provided by third parties.
5. What to Avoid
While using crypto and dApps, you should avoid certain actions. These behaviors should also be avoided on web2, particularly when using financial tools or communicating with authorities. Many users are unaware of this or are unconcerned about the WiFi network they are using while performing sensitive actions.
Being an active web3 user means becoming aware of threats and dangers that you were not previously aware of. If your credit card is compromised, your insurance company and bank can help. However, if you lose funds from a non-custodial crypto-wallet, you won’t be able to recover them.
The two most important things to avoid are performing sensitive actions on insecure networks and believing everything you see on the internet.
Public WiFi
Airports, cafés, and even schools provide public hotspots for their visitors, and because they attract a large number of people, they’re frequently targeted by malicious third parties seeking sensitive information.
WiFi networks that are open to the public can be accessed by almost anyone. Your communications and information can be monitored and even altered. To gain access to your data even more easily, some malicious actors launch fake public WiFi networks masquerading as establishments.
Simply avoid sensitive actions, such as connecting to your bank account or logging into any app when using public WiFi, and don't use cryptocurrency on it.
Don’t Trust, Verify
Some projects' servers on Discord have been hacked in the past, announcing fake mintings or giveaways, causing users to lose funds. Although some users immediately recognized hacks due to differing syntax and writing style from that of the founders, many weren’t able to, resulting in getting scammed.
When you see something unexpected or unusual that requires you to spend your money or connect your wallet, check the project's other social accounts. Events are usually announced in advance, so see if any official announcements have been made and what people are saying on social media.
This is one of the most important principles to understand when navigating web3: Don't trust, verify.
6. Set a Metamask Throwaway Account
When interacting with a dApp or a contract for the first time, it’s common practice to use a disposable Metamask account. This account is completely separate from your main hardware wallet, and will protect you if you interact with a malicious contract or actor.
But what if you want to claim an airdrop based on your current holdings, for example? To claim it, you must use a wallet that contains some valuable NFTs or coins. This is when you must be cautious.
7. Finding Addresses on Etherscan
Etherscan is a fantastic tool and, in my opinion, the best block explorer available. When you’re about to sign your first transaction on a dApp, copy the address you’re about to interact with and search for it on Etherscan. You’ll immediately know if the address belongs to the project in which you are attempting to participate. For example, when I was about to mint a Tubby Cat, Etherscan displayed this address.
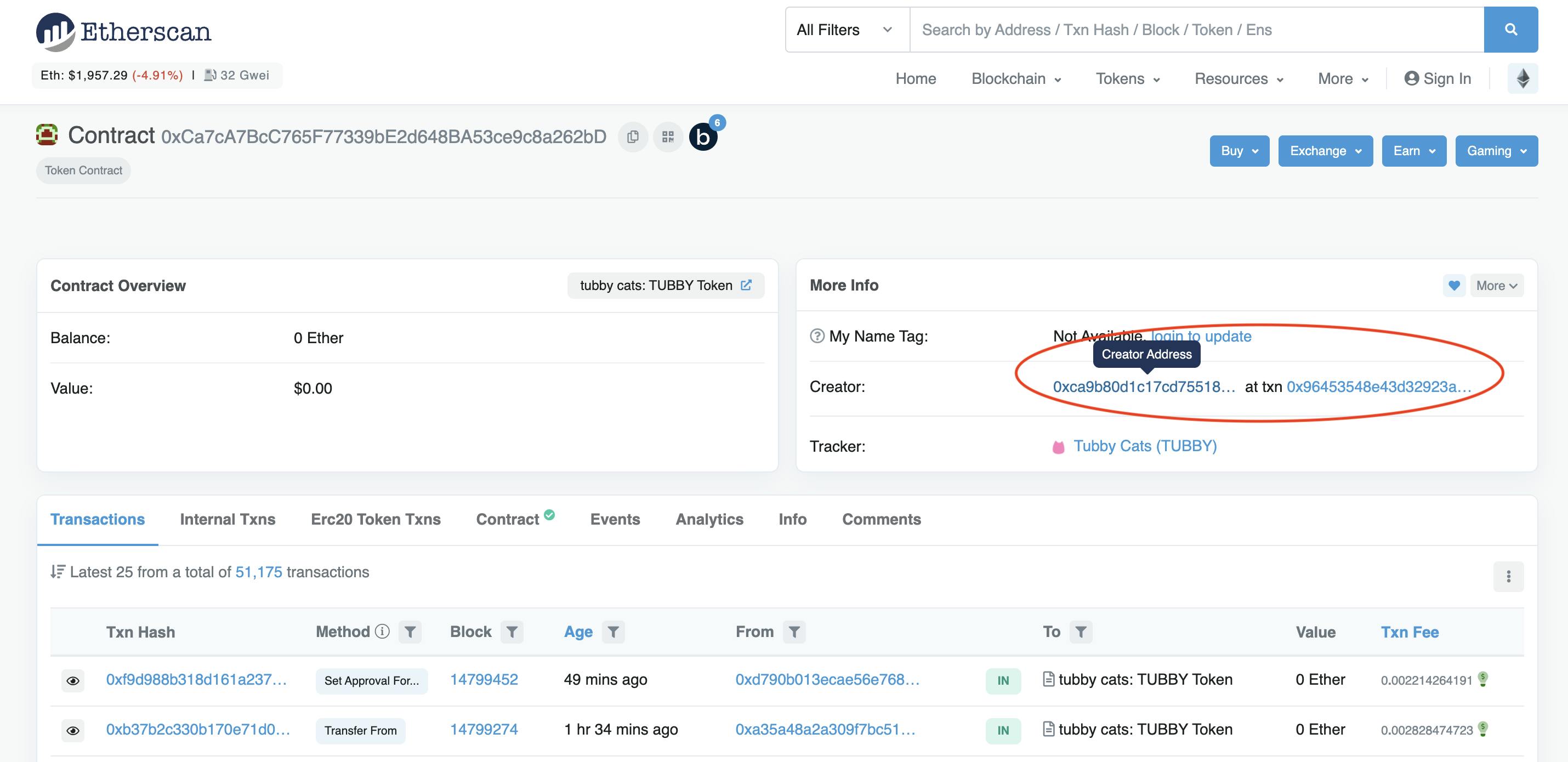
You can also compare the address to those listed in the project's documentation; on an NFT platform like OpenSea, or on the project's Discord server.
There’s a lot to learn from looking at the creator's on-chain activity. Where does the funds come from? Are they associated with rug pulls? Breadcrumbs may be useful in the research phase to easily chart transactions.
You don't need to master these investigation skills to begin your web3 journey, but they’re options for the future if you want to learn more about researching with explorers.
Adding Trusted Addresses to Your Contact List
Once you've found the right address to interact with on a regular basis, add it to your Metamask contact list.
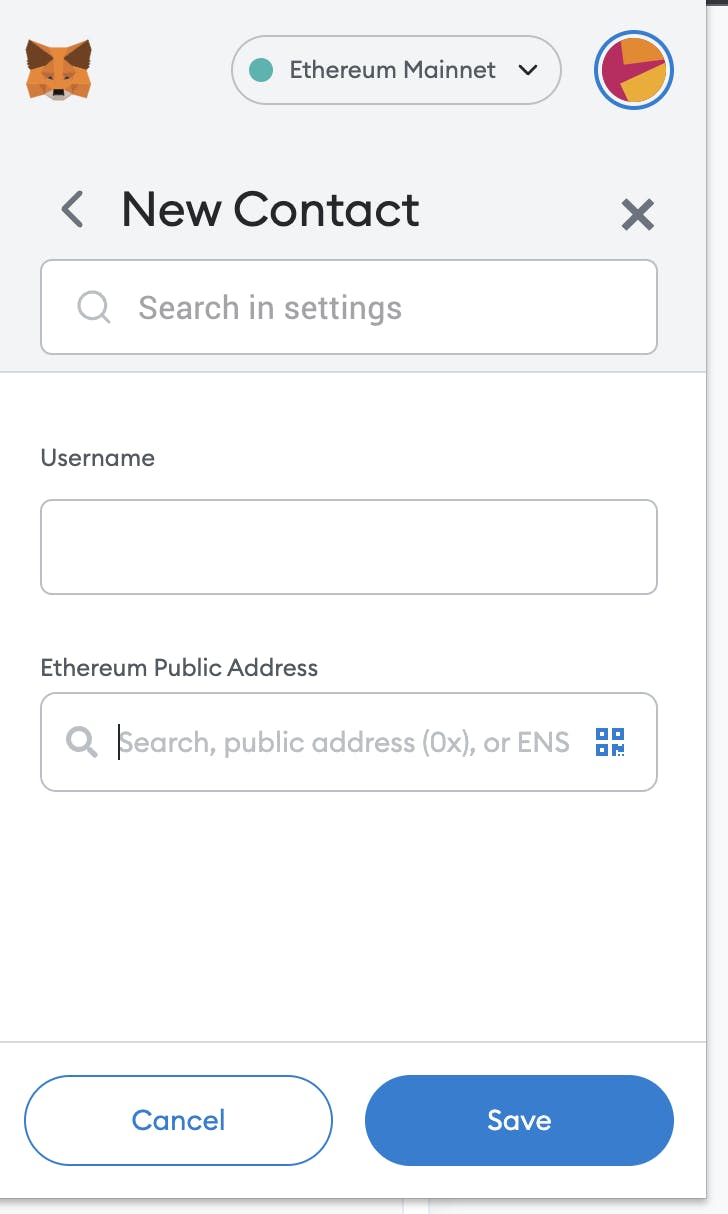
This not only saves you time, but it also prevents Metamask's random rewriting hacks.When the hacker, or a bot, detects a user is about to transfer funds, they try to intercept it.
Assume you want to move some coins to another wallet or put them in a liquidity pool. When the script detects a transfer, it hacks your Metamask by pasting a different address in place of the one you copied.
At a higher level, you’ll learn how to verify where Metamask is getting its data from, but for now, creating a trusted contact list will suffice.
This task may take some time, but if you complete it as soon as you receive the trusted address from Etherscan, it’ll be done. Unless, of course, the trusted address changes, in which case you’ll see a random address. You’ll only need to verify its legitimacy before approving anything.
8. Reading Transactions
Another skill you must learn to stay safe on the internet is to not sign blindly. You must be aware of the actions you’re about to approve. There’s no hardware wallet that can save you if you use it to sign any transaction that comes up.
You can cancel a transaction; for example, if you click on "Connect wallet" but the transaction data shows "Approve unlimited spending of funds", that’s most likely not a good sign.
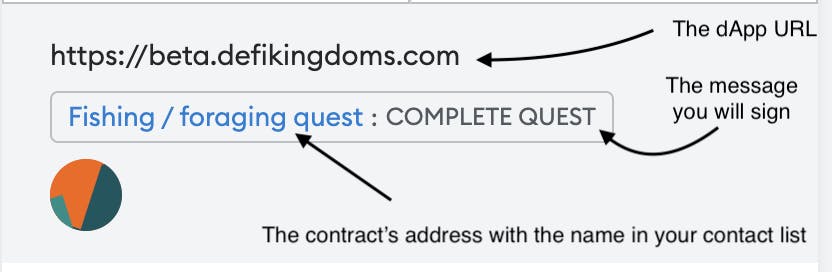
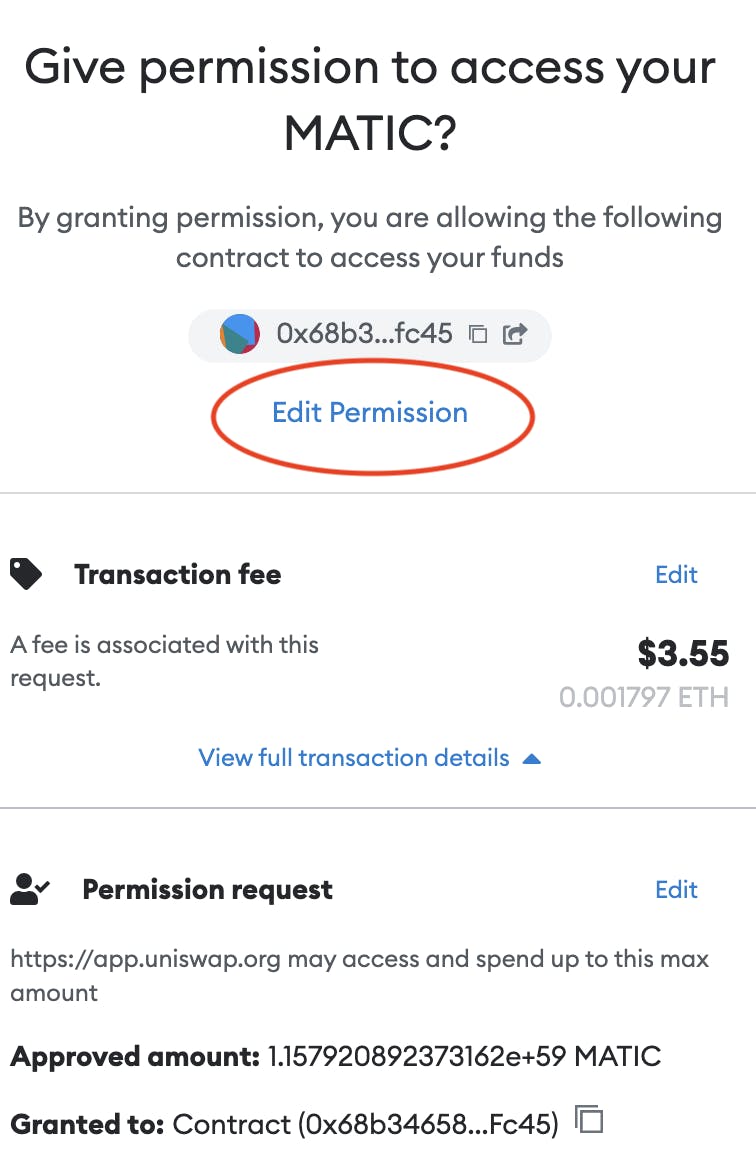
Be Aware of How Much Approval You’re Giving
You can change the spending permission for each transaction. Never give permission for more than you intend to use. You can always change it later.
9. Verifying a Token Address
Because anyone can create a fake token and distribute it on a decentralized exchange (DEX), the token address must be verified on Etherscan. To locate a token address, use Etherscan or another reputable site such as Coinmarketcap.
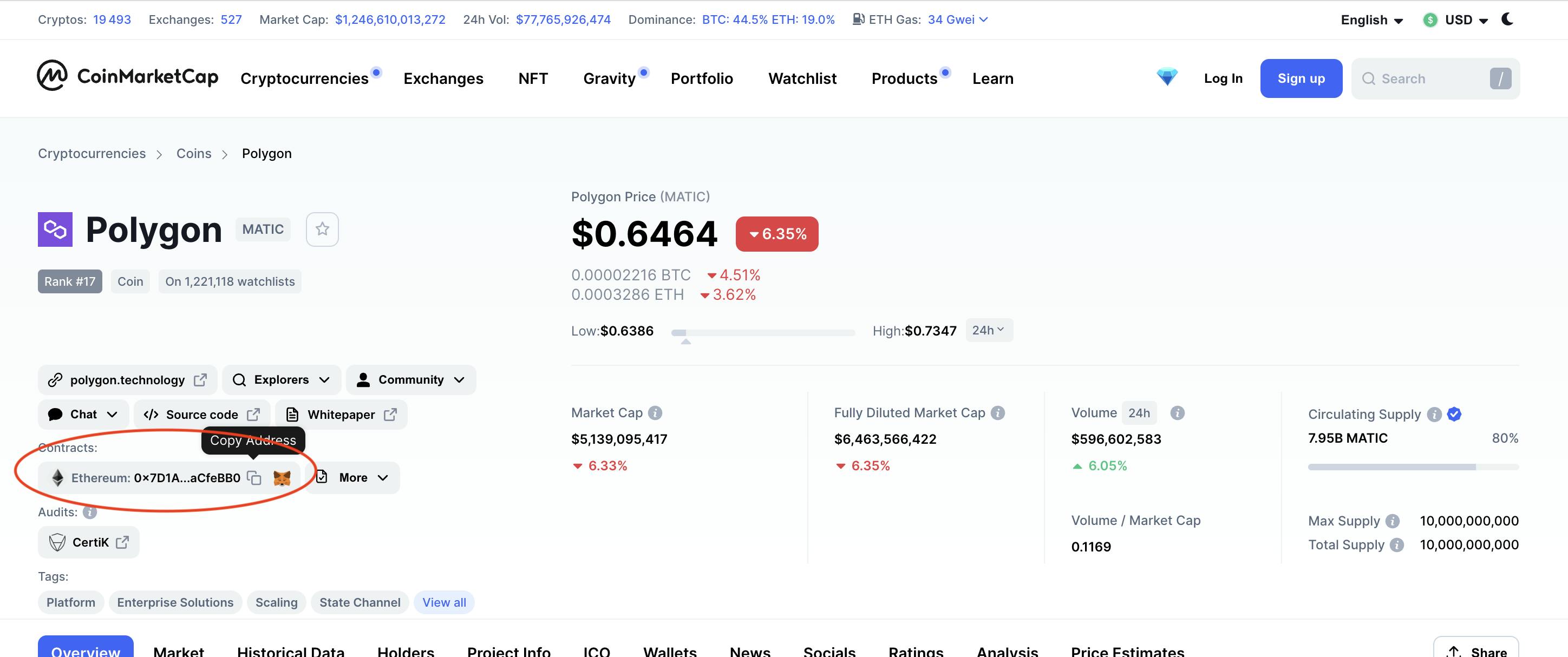
The token address allows you to add it to your wallet and to the DEX lists if it hasn’t been added previously.
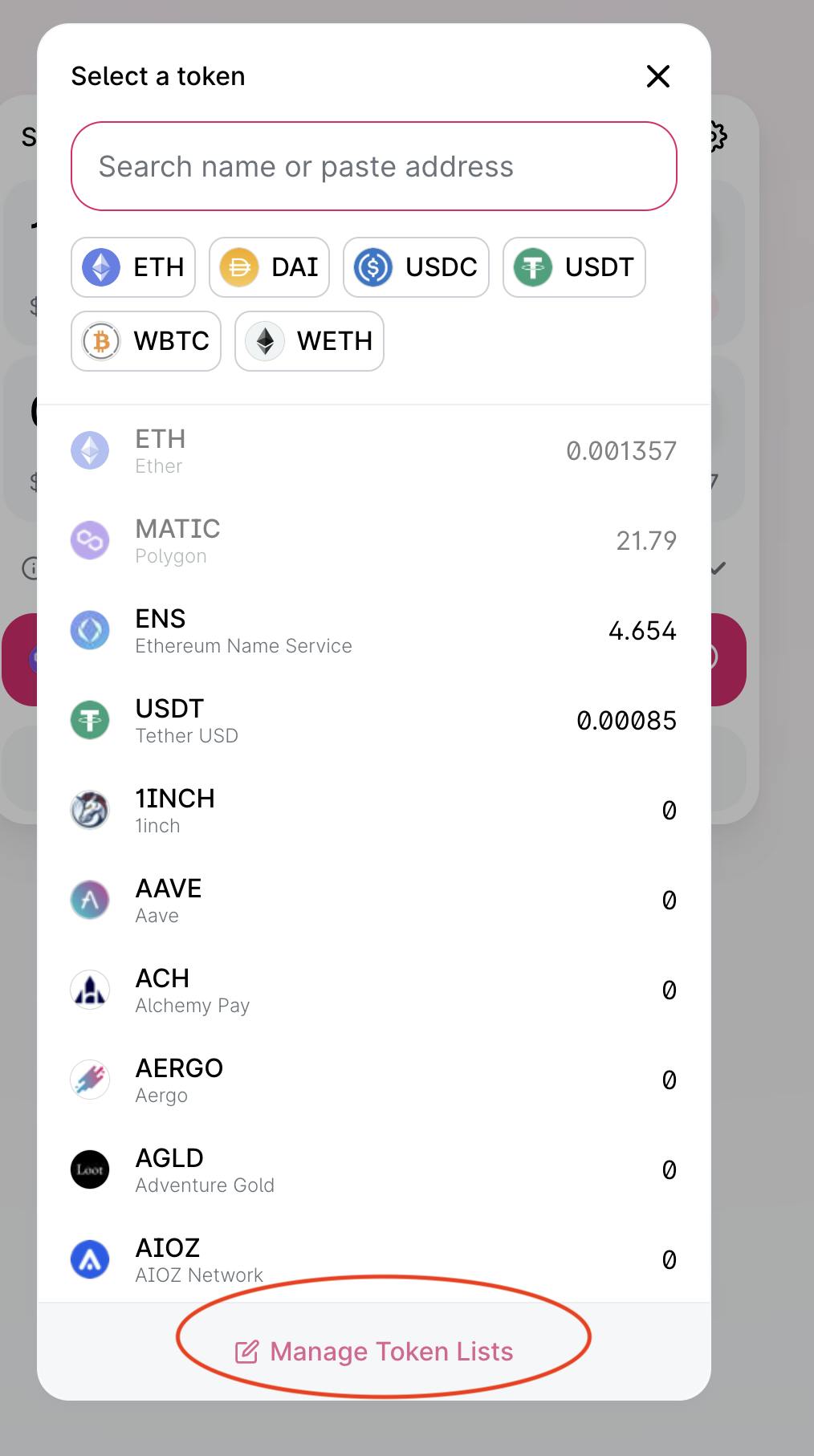
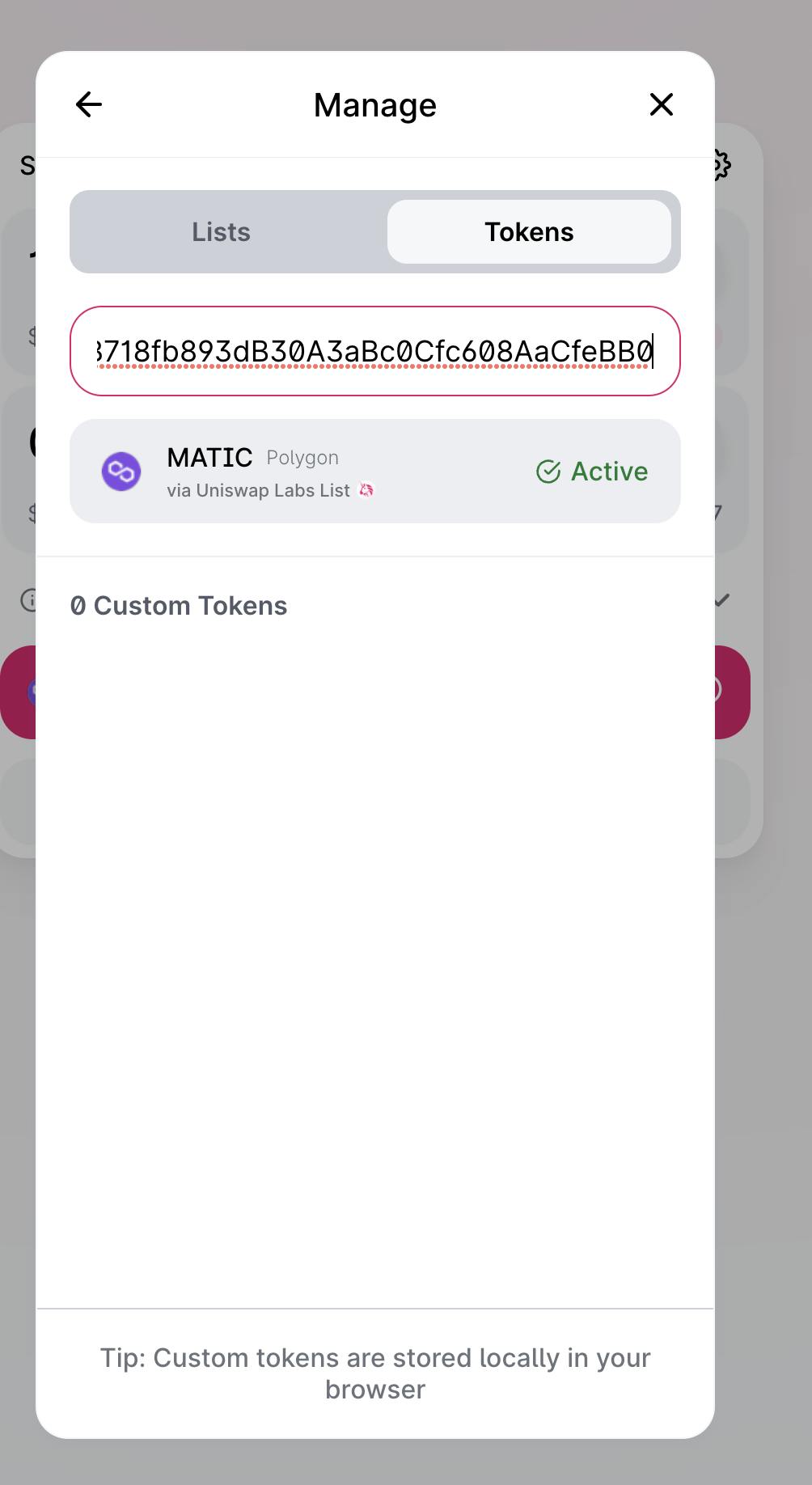
If you’re swapping tokens for the first time on a new DEX, make sure to interact with the right ones this way.
Advanced: Reading Contracts, Audits and Revoking
Now that you understand what you're signing and are a bit more familiar with web3, it's time to beef up your security.
This level can be attained by further verifying tasks and systematically revoking what you aren't using. Smart contracts rule web3, and we'll teach you all about them.
10. Smart Contract Verification
The majority of your web3 activity consists of approving smart contracts with your wallet. The majority of web3 vulnerabilities are found in smart contracts, which are being exploited.
Because the majority of web3 is open source, exploits are quickly identified by the community. The contract is then revoked by users while it’s being patched.
It should be noted that there are no simple methods for determining the security level of any contract before an exploit occurs. As is always the case, vulnerabilities emerge after an attack.
Although open source code and transactions help the community respond quicker, there’s a drawback: Anyone watching the exploit in progress may decide to replicate it as well. This is why some codes are no longer open source, but instead, are audited by trusted third parties. Let's look at how you can validate the contract you’re interacting with.
Find the Contract
Any smart contract, like your wallet, is associated with an Ethereum address. If you use a hardware wallet, click on it and wait for the Metamask pop-up to ask for approval. Instead of accepting, copy and paste the address.
You can also find contract's addresses on aggregators, like DeFiLlama.
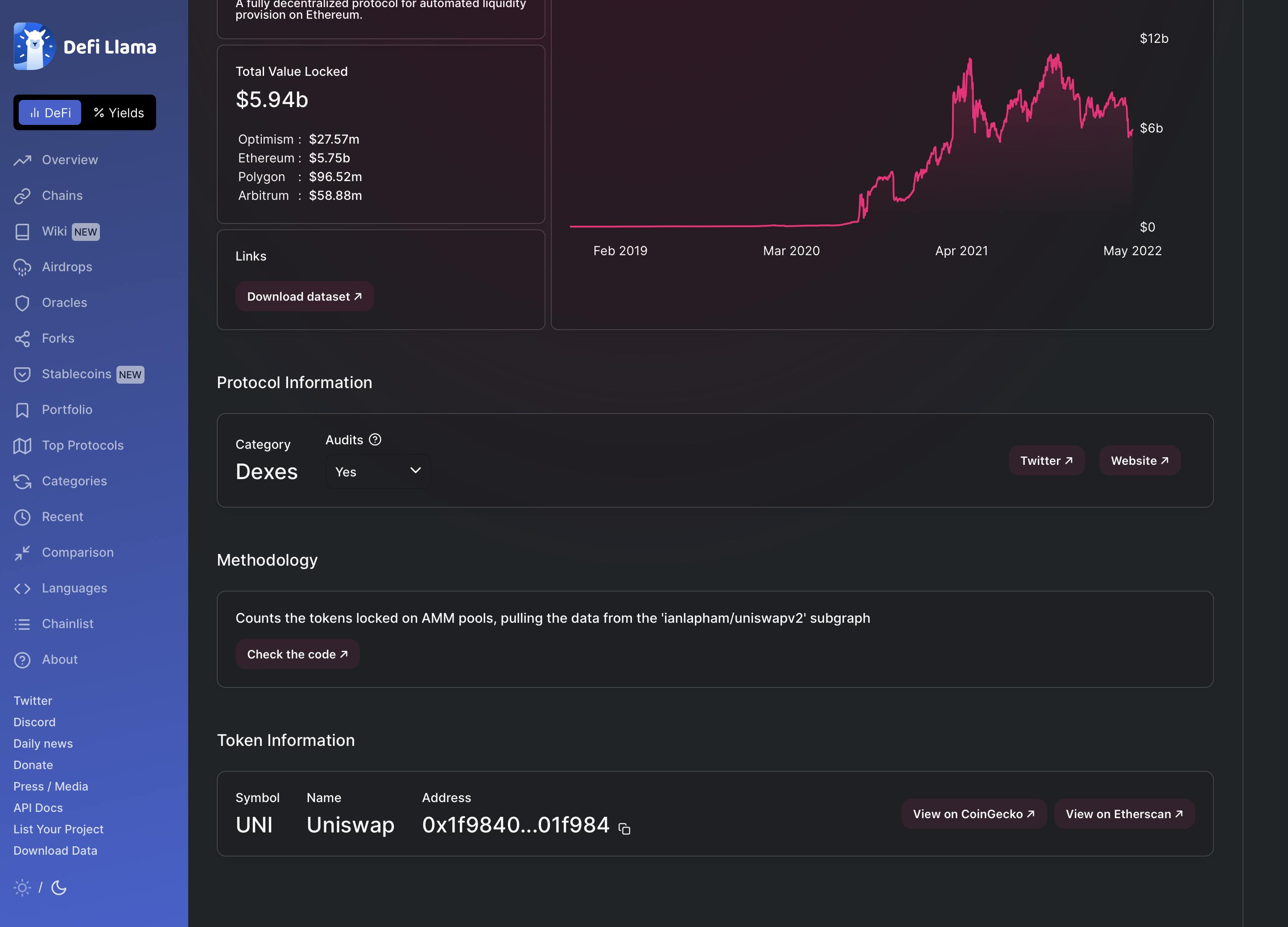
Once you have the contract's address, enter it on Etherscan. In this example, we'll look at the Uniswap contract. Let's double-check who we're giving permission to spend our MATIC with.
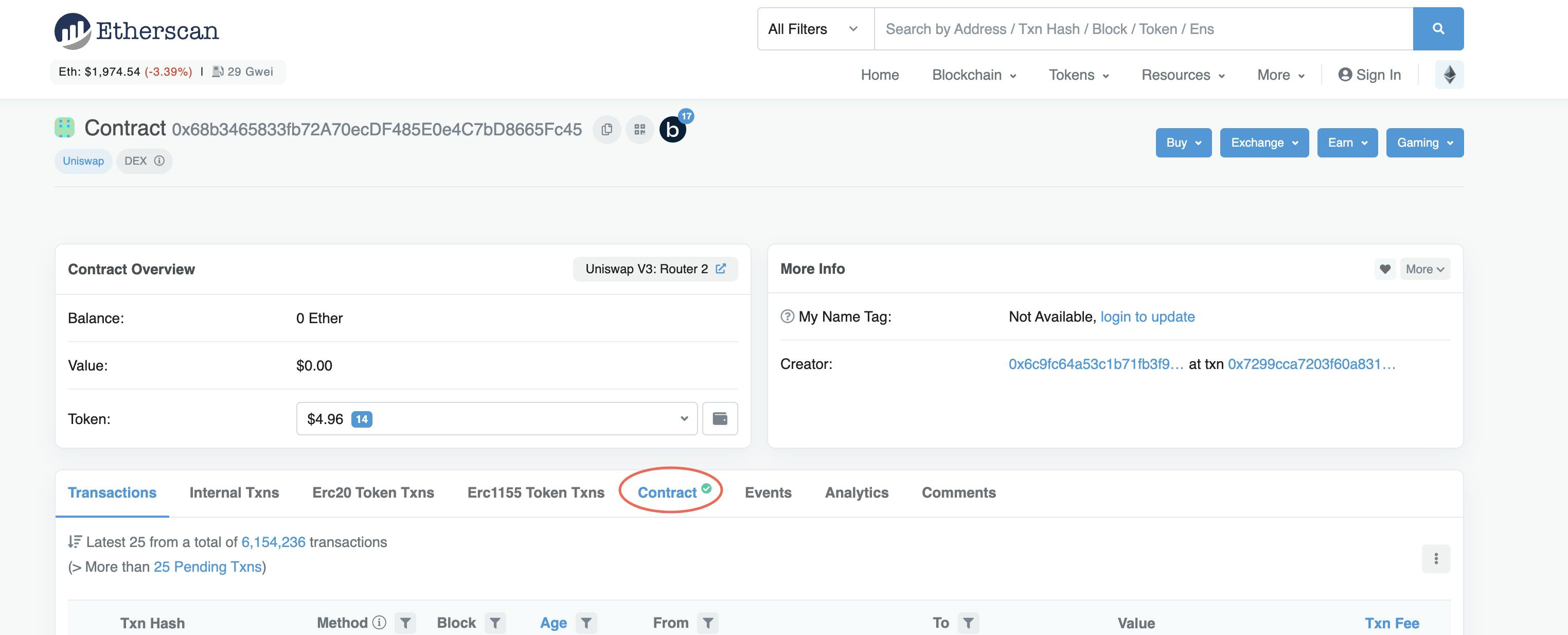
The first thing you see is that the contract is verified, which means that only the contract's owners can modify it.
Check the Contract
The Uniswap contract is open source in this case, meaning, any vulnerabilities or malicious functions can be discovered by anyone. Even if you don't know how to interpret the code, a quick internet search will tell you what you're getting into.
Look at the functions defined in the contract if you're feeling nerdy and willing to dig into the code. What exactly are we looking for? Any operation that:
Allows access to a specific token,
Does not permit us to withdraw funds from a liquidity pool,
Masquerades as a deposit, but sends our tokens to a hacker's wallet.
Look especially for the ‘SpendWalletWETH’ function (this is for WETH, but could apply to any other token) and what causes it.
If you'd rather die than read a single line of code (understandable), you can use DeFiSafety or any other third-party services that assess and publish the risks associated with a project, dApp, or contract.
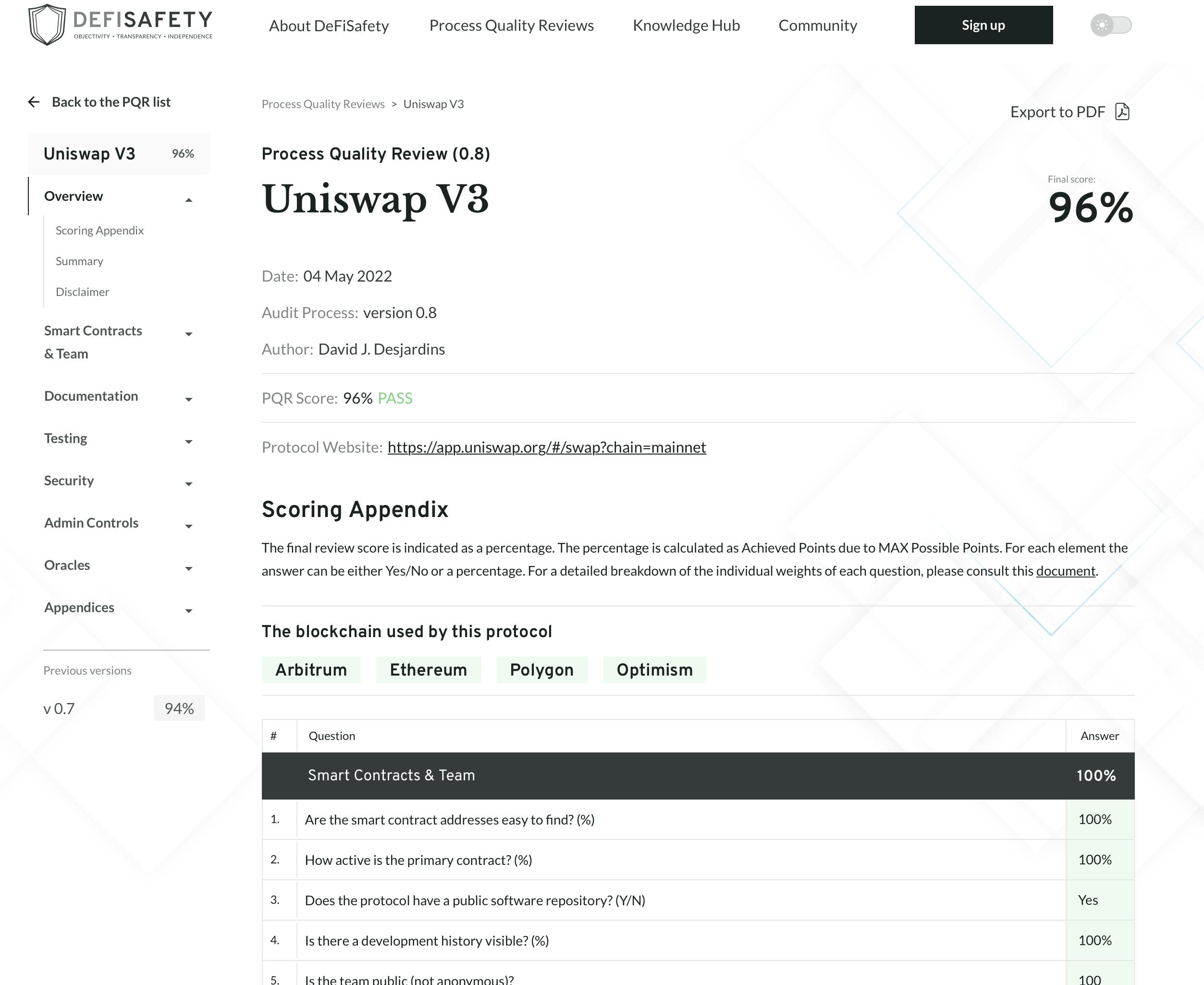
It's best not to rely on yourself, instead look into what third parties and developers are saying about a protocol you want to try. The greater the transparency of the documentation and audits, the better.
11. Verifying Metamask Data
Every day, new methods of stealing assets are emerging, and this one is possible even if you use a hardware wallet. In this case, the thief targets owners of large amounts of cryptocurrency. The funds are stolen by intercepting a transaction and changing the recipient's address. Remember how I said you should make a contact list? This is the reason why.
When you want to transfer funds between wallets and don't pay attention to the transaction details before signing with your hardware wallet, the hacker injects a code that rewrites the transaction, changing not only the address, but also the amount in order to drain the wallet in one move.
If you aren’t familiar with the Metamask code base, the hack isn’t difficult to spot in its settings. Navigate to Chrome's settings, select “Extensions”, and enable “Developer Mode”.
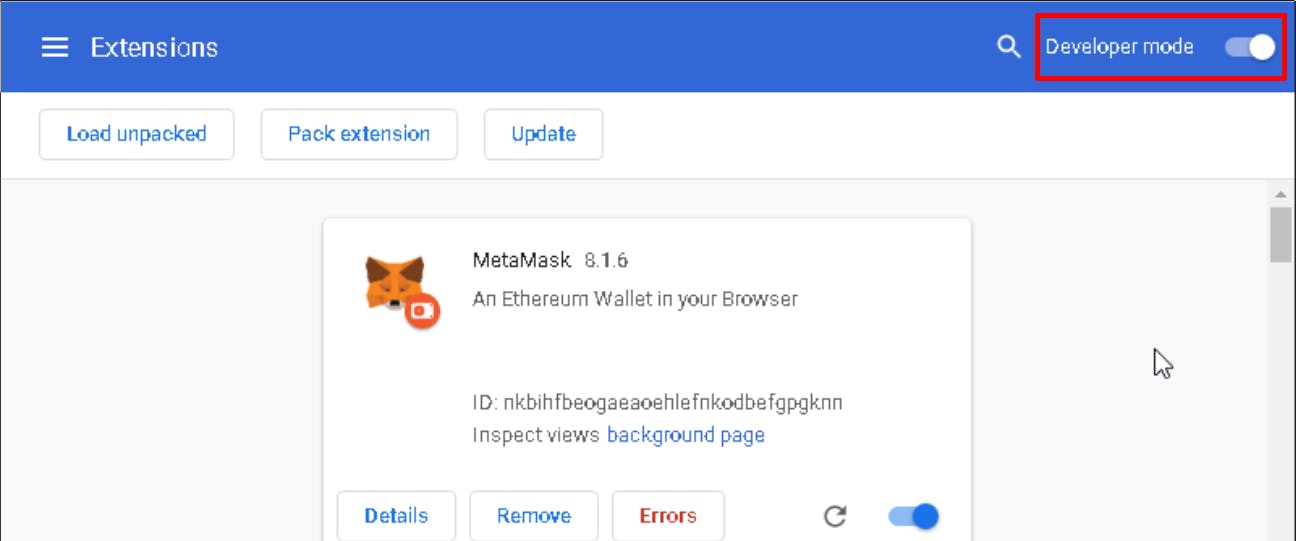
If the source is Chrome Web Store, you’re fine.
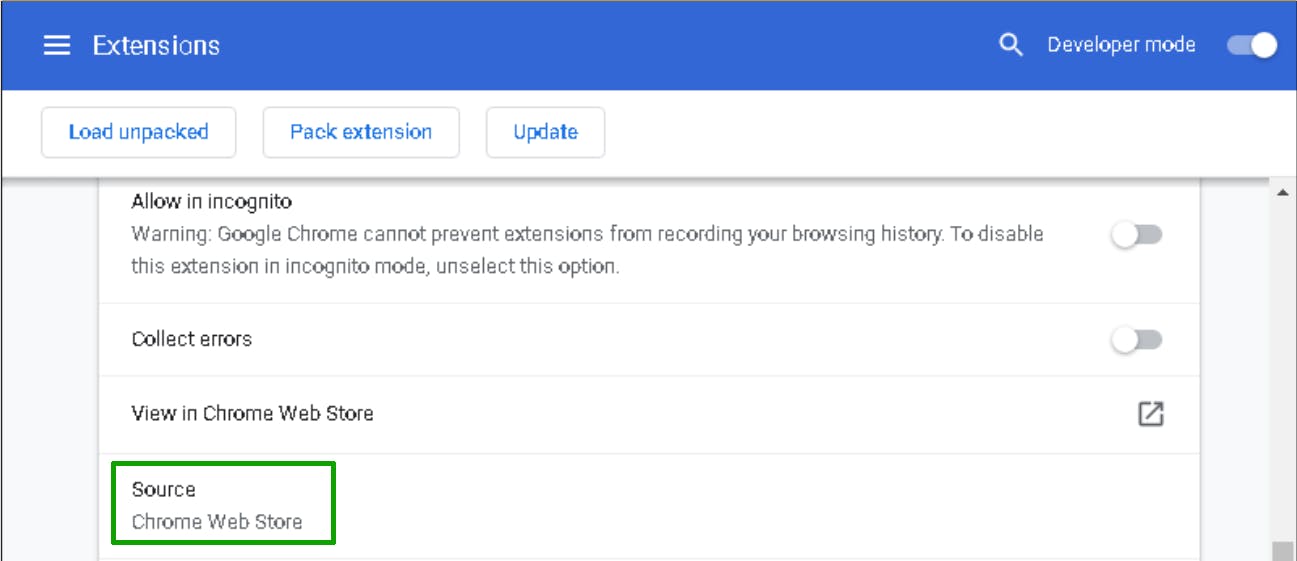
When in doubt, double-check and always use Web Store extensions. Read transactions carefully before signing, and cancel anything that appears suspicious.
12. Revoking Permissions
You must approve smart contract permissions in order to interact with dApps. You've discovered that smart contracts allow you to change the amount you approve, and now you'll develop a new habit for good wallet hygiene: Revoking token approvals.
Token approvals are an attack vector for a variety of scammers and hackers who will exploit code flaws to drain funds (this happened to Wormhole. This is because the default approval is usually set to “unlimited”, and users don't bother to change it. Make a habit of reviewing your approvals on a monthly basis and discarding those you don't intend to use.
Revoking With Network Explorers
Keeping track of your existing approvals is simple. Simply navigate to the "Approval" section of your network explorer, such as Etherscan, BSCScan, or Polygonscan.
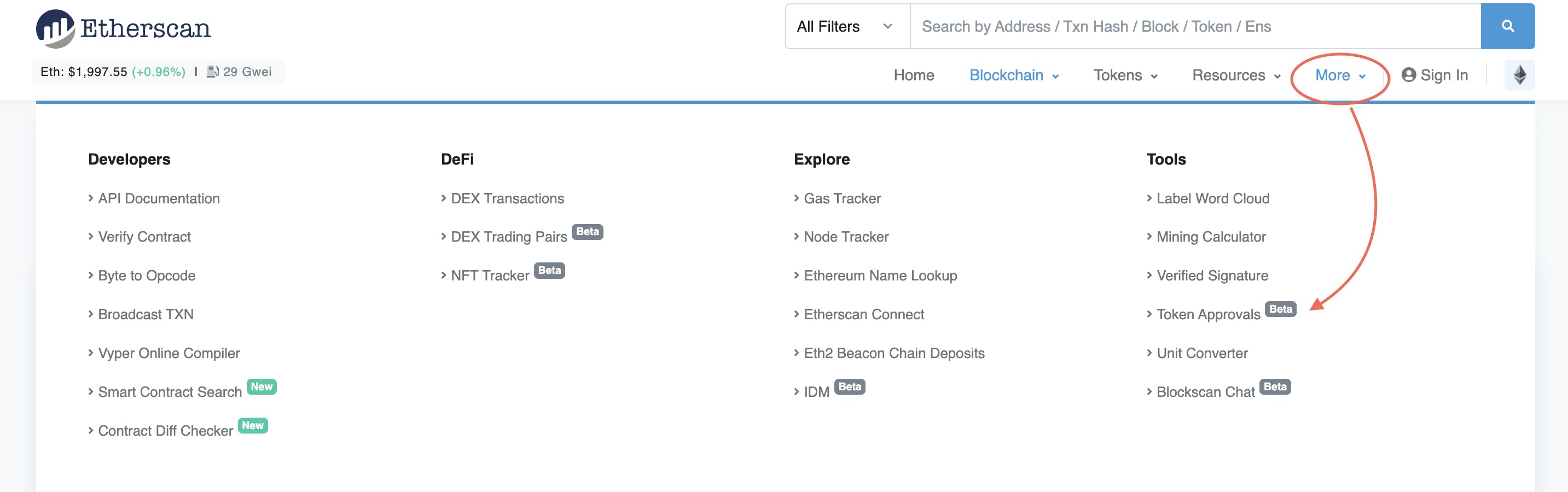
Connect your wallet and revoke any token approval. You can also use sites like Revoke, Unrekt and Approved Zone.
Conclusion
Navigating web3 in its early stages safely requires a shift in habits. In order to protect their funds, users must be cautious navigating web3 because its use entails the transfer and manipulation of cryptocurrencies, as well as the irreversible nature of the transactions.
Using DeFi tools and participating in web3 projects can earn you a lot of money. But equivalently, a large sum of money can also be lost due to a single error.
In web2, users create content and hand over ownership to a few centralized organizations that profit from it. In web3, acquiring power, ownership, and wealth comes with being able to take huge responsibilities and accountability.
This blog is a part of the Hashnode Web3 blog, where a team of curated writers are bringing out new resources to help you discover the universe of web3. Check us out for more on NFTs, blockchains, and the decentralized future.

