Today, our lives are increasingly connected to the apps and services we use.
An eCommerce store to shop online, a social network to interact with, an email system for work communications—the list goes on.
Using these services requires proving our identity and authorizations. While we're used to giving out low-level identity information, such as names and email addresses, other services may require a high-level ID like a Driver's License.
However, current identity management systems have several flaws.
Not only are they centralized, with service providers storing user data, but they are also risky since malicious actors can breach servers and steal your information.
Decentralized identity improves on existing identity management standards and gives users greater control over personal data.
In a decentralized identity framework, individuals store their identity information and choose what to share with third parties.
Because decentralized identifiers are stored on distributed ledgers and blockchains, they are tamper-proof, secure, and instantly verifiable by anyone.
This reduces the need to store identity information in servers and makes it easier for users to access services seamlessly.
This article explains what decentralized identity means in detail, how it works, and why it matters. We'll cover key concepts like decentralized identifiers and decentralized authentication and explore existing decentralized identity projects.
Let's dive in!
What Does Decentralized Identity Mean?
Decentralized identity is a new form of identity and access management (IAM) that de-emphasizes centralized storage of user information. Decentralized identity bolsters individuals' control of their data—hence it is also known as self-sovereign identity (SSI).
In plain English, a decentralized identity allows you to own your identity. So how does it work in practice?
Your identity is a collection of attributes and credentials that uniquely describe you. Some identifiers may be self-owned, like your name, DOB, email address, username.
And others may be issued by institutions; for example, a university degree, Driver’s License, or passport number.
In decentralized identity management, users store credentials and personal information in a “digital wallet.” Just like a real-life wallet, a digital wallet holds your identifiers, such as your license or ID card.
Decentralized identity distributes the storage of identity information across a system of distributed computers, like a distributed ledger or blockchain.
The use of distributed ledgers to hold identity elements renders them immune to alteration and theft. So, even though your identity information is recorded in electronic format, it cannot be altered, stolen, or deleted.
The transparency inherent in distributed ledgers makes identity information instantly verifiable without necessarily relying on the issuer.
Here’s a brief illustration of how decentralized identity works:
An organization (the Department of Motor Vehicles) wants to issue you (the user) a credential (Driver’s License). You send your wallet address, which is a specific location on the distributed ledger or blockchain for storing data. The DMV then sends the credential to your digital wallet, signing the transaction with its private key.
Now, you can share this credential anytime you need to establish your identity—for example, while completing a loan application. Using a trusted utility, the other party can check the validity of your credentials. In this case, the utility checks the public keys and transaction details to confirm the issuing organization and date of issuance.
Note that the information itself is not stored on the blockchain. Instead, the blockchain generates an immutable record of the transaction that saw the information pass from the issuing organization to you. This “digital fingerprint” (also called a hash) is unique to each credential and can reliably prove your ownership.
The various players in a decentralized identity ecosystem include:
Users: Individuals who own and use pieces of identity information. Users like you can keep various identifiers in a digital wallet and share them on an as-needed basis.
Issuers: Organizations and institutions that issue credentials and claims to users. This can be your local Tax Office, an employer, an academic institution, and any entity that can issue identity information.
Verifiers: Third-parties who need identity information to establish trust and grant access to services. For example, an online shop may need proof of your age or citizenship before allowing you to purchase certain items. Any information you provide would need to be verified properly.
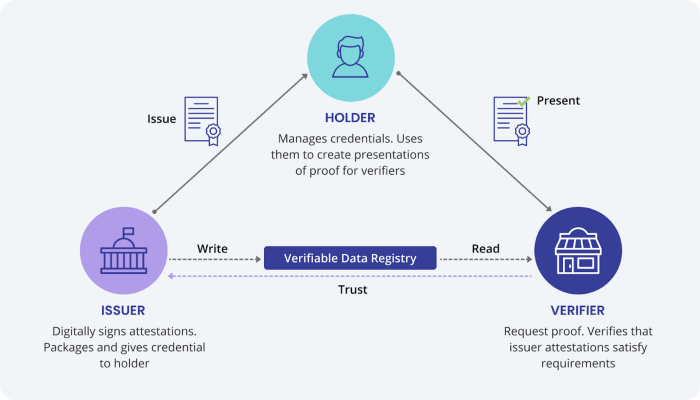 An overview of the decentralized identity ecosystem. Source: Affinidi.com
An overview of the decentralized identity ecosystem. Source: Affinidi.com
How does a Decentralized Identifier Work?
The World Wide Web Consortium (W3C) defines a decentralized identifier (DID) as a form of verifiable, decentralized digital identity. A DID can be created for any entity, including an organization, individual, or even a device.
Designed to be user-controlled, DIDs are stored in a decentralized architecture, like peer-to-peer networks or a distributed ledger instead of a centralized registry. As such, a DID is cryptographically secure, resistant to changes, and verifiable without depending on the original issuer.
Decentralized Identifiers and Verifiable Credentials
Verifiable Credentials complement DIDs and power decentralized identity management. The W3C defines verifiable credentials as "verifiable credentials represent statements made by an issuer in a tamper-evident and privacy-respecting manner."
When a university issues an academic certificate, it is "claiming" that the recipient has undergone education for a certain period. Similarly, a vaccination passport is a claim that you have received the vaccine.
While these claims already exist as physical documents, using them online poses several problems. Let's imagine a Know Your Customer (KYC) process requires uploading your degree Driver’s License to verify your age during a KYC registration.
First, the service provider cannot confirm the claim's authenticity. Second, your private information is now stored on multiple servers, increasing the risk of identity theft. Third, you need access to a physical copy of your license—if you lost it, then you cannot prove your identity.
Verifiable credentials solve these problems in three ways:
- Using zero-knowledge proofs to prove the validity of claims data without revealing private information
- Using public-key cryptography to verify claims issuers
- Storing claims information on Verifiable Data Registries (blockchains, distributed ledgers)
Using our initial example, you wouldn't need to upload the entire Driver's License during the KYC. Instead, you could just share a link to the Verifiable Credential.
Verifiable Credentials use zero-knowledge proofs to protect the privacy of ID holders. Zero-knowledge proofs help prove the authenticity of information without revealing the entire information to a third party.
Let’s use the example of a Driver’s License to explain how ZK-proofs could protect your privacy:
The service provider won’t actually see your birth date listed on the license. However, the credential will identify the issuer (the DMV) via the public key. Since the DMV only issues licenses to individuals within a certain age-range, then we can assume that your age claim is correct.
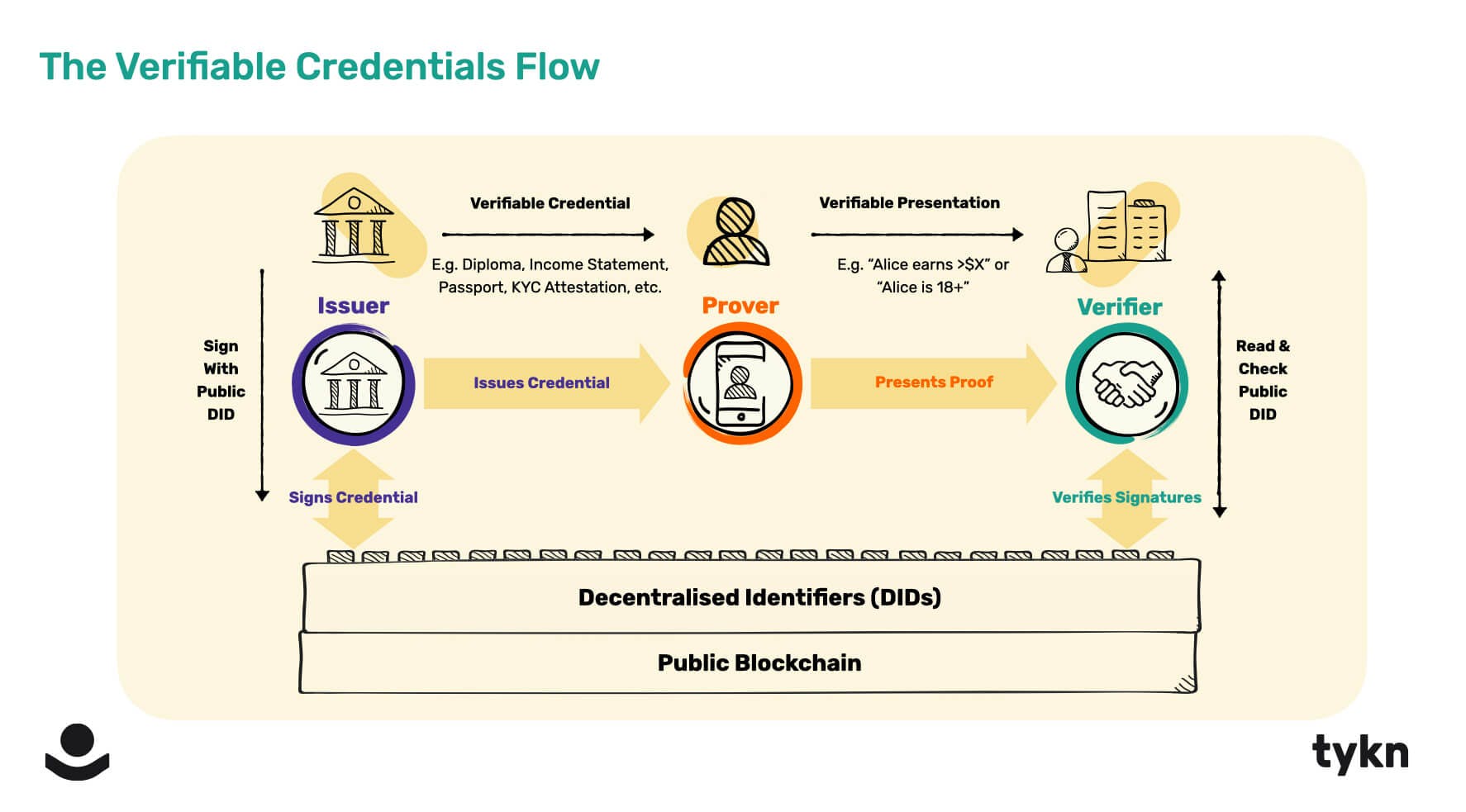 How Verifiable Credentials (VCs) work. Source: Tykn.tech
How Verifiable Credentials (VCs) work. Source: Tykn.tech
VCs are immutably stored on the blockchain, meaning you can access them insofar as you have your wallet and private keys. They cannot be destroyed, modified, stolen, or deleted. More importantly, they aren't under the control of the issuing organization.
Verifiable Credentials are an important building block of decentralized identity management. With VCs, we can create digital versions of physical credentials and use them online without having to disclose more information than necessary. Third parties can easily confirm the veracity of these credentials without relying on the issuing institution.
What is Decentralized Authentication?
The COVID-19 pandemic has rapidly accelerated the shift to a digital lifestyle. Now, you may choose to do things like banking, videoconferencing, communication, and shopping from the comfort of your home.
Accessing these platforms requires verifying your identity and permission to use those services. For example, a banking site may ask you to provide an email address and a password.
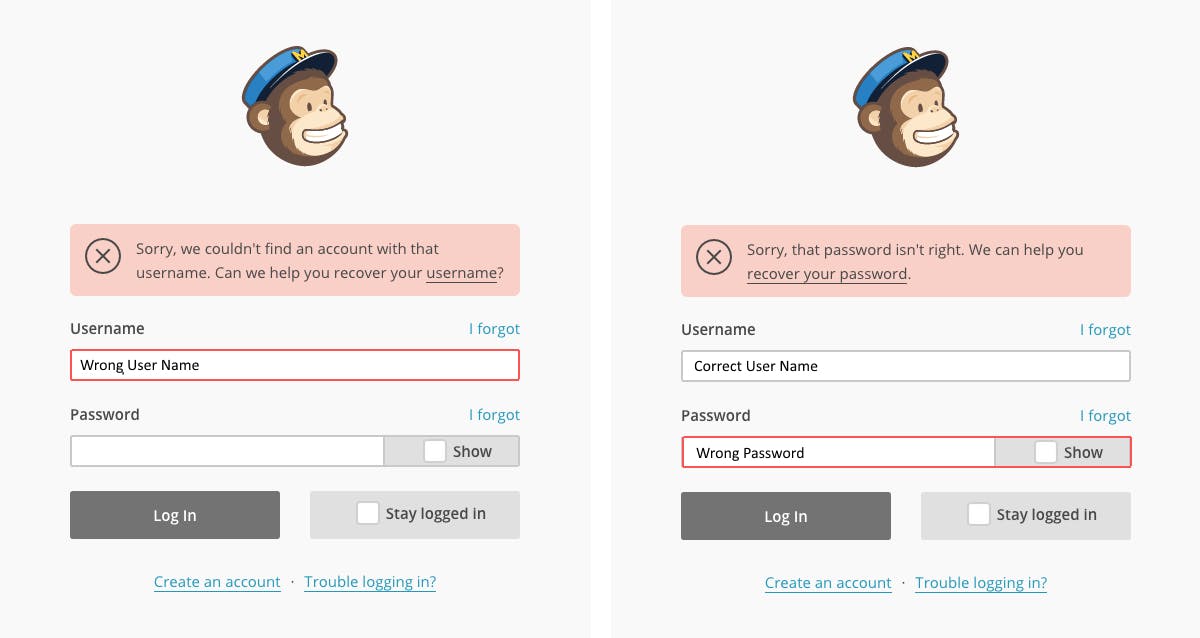
However, traditional authentication can be quite problematic. Not only do you have to create multiple logins for different services, but you must remember each one, or risk losing access.
Users may reuse passwords across multiple sites to make online authentication easier, but that only increases the risk of identity theft. If a hacker steals one password, they can easily impersonate you on a dozen different platforms.
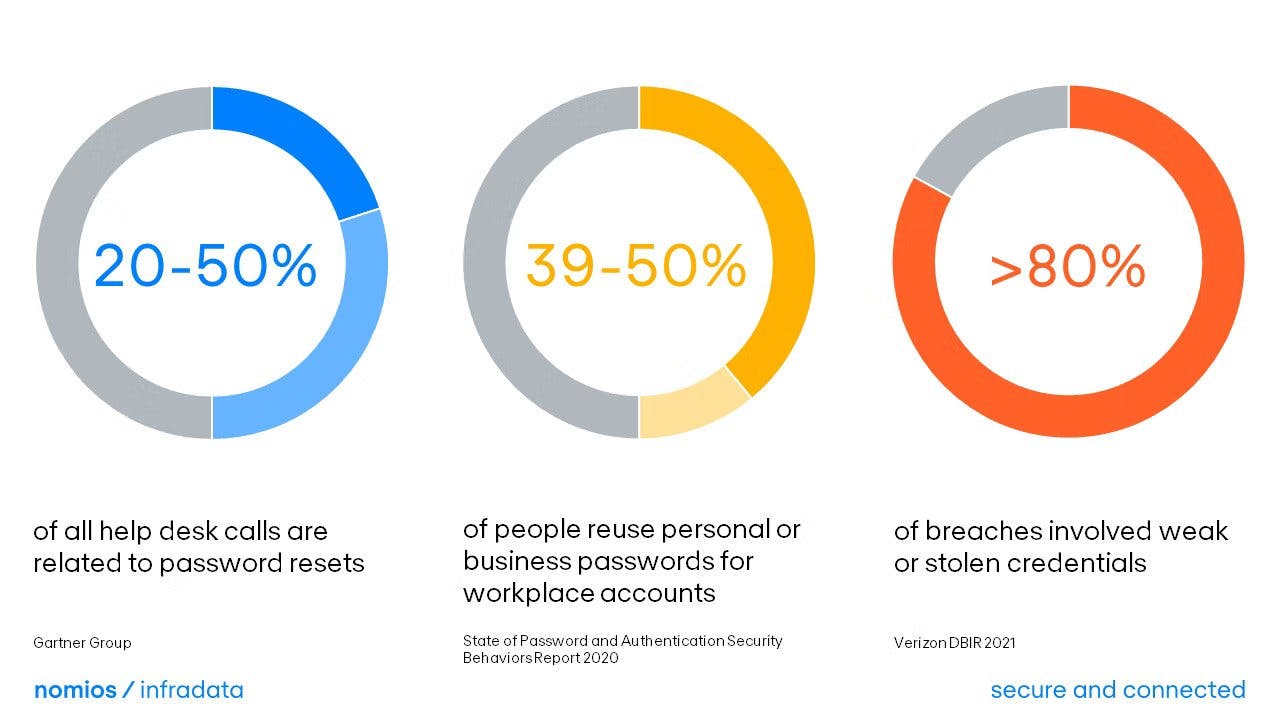 Problems with password-based authentication. Source: Nomios.com
Problems with password-based authentication. Source: Nomios.com
Federated authentication is one of the current solutions designed to make online authentication easier and safer. Here, a group of entities agrees to rely on one source for identity information. A good example of federated authentication is logging in to a site with your Facebook or Google account.
But federated authentication is hardly a silver bullet. Your identity information is still hosted on a central server (Facebook and Google), so the risk of a data breach or identity theft is still there.
 Federated authentication systems rely on third-party services to verify identity. Source: apievangelist.com
Federated authentication systems rely on third-party services to verify identity. Source: apievangelist.com
Decentralized authentication is a newer concept where users can gain access to online services using verifiable credentials. Say you wanted to access an online banking service. Instead of submitting ID documents, you could submit a Verifiable Credential from a government body to prove your identity.
This removes the need for the bank to request and store your information before granting you access. And you won’t need an account to login in the future since the service provider can issue a Verifiable Credential for ongoing verification. Logging into the site would be as simple as connecting your digital wallet!
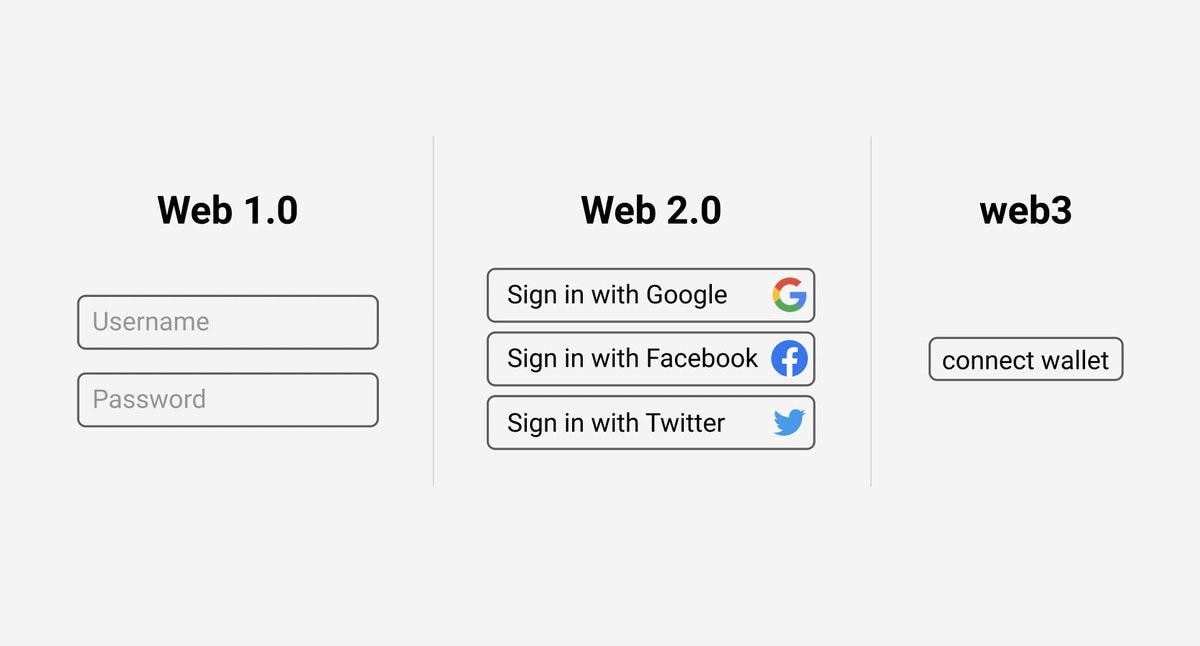 Decentralized authentication vs traditional authentication. Source: Coingeek.com
Decentralized authentication vs traditional authentication. Source: Coingeek.com
Why Is Decentralized Identity Important?
Decentralized identity promises to revolutionize how we share our data. Here are some of the benefits of decentralized identity management:
1. Easier Authentication
Decentralized identity can eliminate passwords and annoying multi-factor authentication protocols. With password-less authentication, using online services becomes easier and faster since you don’t need to enter long passwords.
Organizations can quickly verify user identities without forcing them to undergo burdensome KYC processes. Loan applications, government registrations, website sign-ups—all of these would happen faster because service providers can verify your identity via third-party utilities.
2. Better Data Safety
As explained earlier, many organizations require new users to submit identity information. That wouldn't be a problem, except that companies are provably sloppy at safeguarding user data. Modern data centers are honeypots for hackers, and data breaches have led to massive losses for businesses and consumers.
A decentralized identity framework removes the need for centralized storage of user information. This is especially important when dealing with personally identifiable information (PII), such as your medical history or credit card information. Sensitive ID information would be safely stored in your digital wallet, allowing you to share it when necessary.
Decentralized identity systems will also reduce cases of identity theft. Your personal information and credentials aren’t sitting in a data silo for a hacker to steal. Neither do you need passwords for website access, so phishing attacks will inevitably fail.
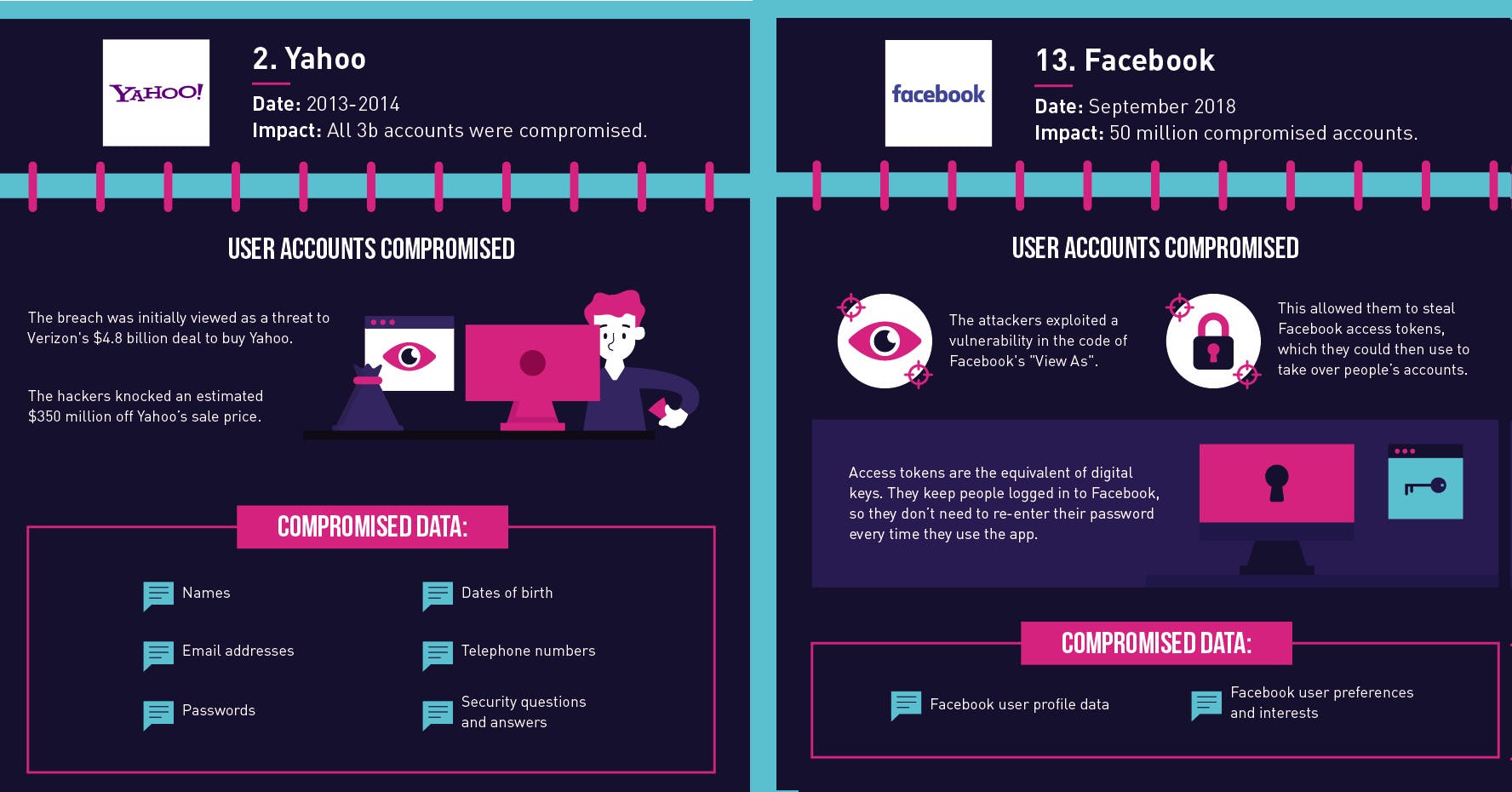 Decentralized identity can reduce data breaches and ID theft. Source: Visualcapitalist.com
Decentralized identity can reduce data breaches and ID theft. Source: Visualcapitalist.com
3. Lower Data Management Costs
According to statistics, global businesses spend between 4-7% of their revenue on managing user data. Companies are spending billions on database management annually, but these funds certainly have better uses.
Decentralized identity lets users store personal data, taking the burden off organizations. With no data centers to manage, service providers can reduce running costs and re-invest funds into improving service offerings.
4. Regulatory Compliance
From the European Union to the USA, regulators are tightening data privacy laws. Legislations like the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) have created a regulatory minefield that organizations must navigate or risk sanctions.
A decentralized identity framework absolves organizations of building up databases to store user information. As a result, companies can better comply with data privacy laws and avoid drawing the ire of regulators.
5. Richer User Experience
Think about the difficulty of managing different identity profiles for the dozens of services you use. What if you could use the same identity across different platforms without worrying about creating new logins repeatedly?
With decentralized identity, an interoperable internet where you can use one ID for different sites could become the reality. You’d be able to seamlessly switch between services by connecting your wallet.
 Decentralized identity can improve users’ online experience. Source: Babich.biz
Decentralized identity can improve users’ online experience. Source: Babich.biz
6. Personal Ownership and Control of Data
Decentralized identity is described as self-sovereign identity because it puts control of personal data in the hands of individuals. Your private information doesn’t become the property of third parties, to be stored in centralized databases.
In a decentralized identity system, you decide what information is privy to third parties. Zero-knowledge proofs further protect your privacy by eliminating the need to reveal sensitive information. For example, you could prove your age without showing your address or nationality to a service provider.
Since Verifiable Credentials are digital, your identity becomes portable. You don’t need to carry around a Driver’s License or an immunization passport to prove your vaccination status.
VCs can be independently verified, so you’ll never have to rely on an issuer to verify your claims. At all times, your personal information and credentials remain under your control.
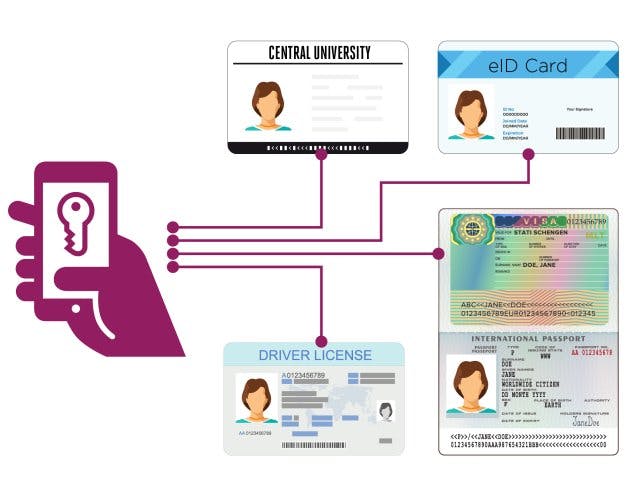 Decentralized identity allows users to retain control of credentials. Source: gsma.com
Decentralized identity allows users to retain control of credentials. Source: gsma.com
7. Greater Trust Between Organizations and Users
Trust is the glue that holds the relationship between companies and customers. When two parties trust each other, mutually beneficial relationships can be established.
However, trust is a scarce commodity in our world today. Consumers don’t trust companies not to collect—and potentially mismanage—their data. And organizations are wary of users who may commit identity fraud—hence they require lengthy verification processes before providing services.
Decentralized identity can solve both problems and create unprecedented levels of trust between users and service providers.
Cryptographically secure and verifiable credentials can help companies verify user identities and accelerate customer onboarding. And users won't worry about data breaches and identity theft while interacting with service providers—a win-win for everyone involved.
An Overview of Decentralized Identity Projects
The decentralized identity movement has been gaining for some years now, with several high-profile organizations leading the push. Microsoft, Hyperledger, and the Decentralized Identity Foundation are among the most visible companies in the industry currently. Below is an overview of their projects:
Microsoft Decentralized Identity
Microsoft entered the fray in 2014 by releasing the Azure Active Directory, a service enabling the adoption of decentralized identifiers and verifiable credentials. It uses the Identity Overlay Network (ION), a side-chain built atop the Bitcoin blockchain to securely manage user identities.
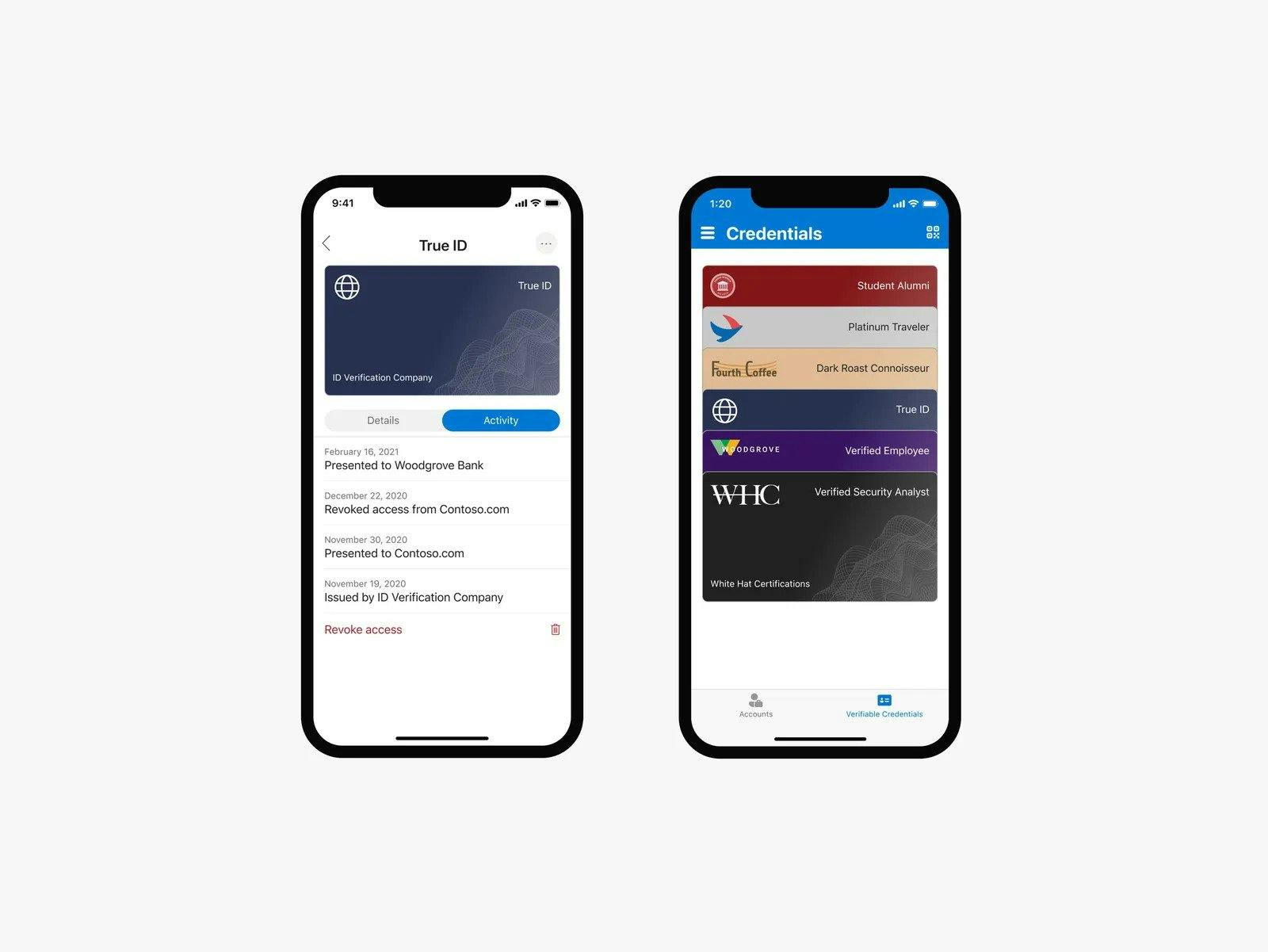 Users can share verified credentials using Microsoft decentralized identity. Source: Wired.com
Users can share verified credentials using Microsoft decentralized identity. Source: Wired.com
Hyperledger Decentralized Identity
 Source: Hyperledger.org
Source: Hyperledger.org
Private blockchain Hyperledger has created several tools to help developers and organizations build decentralized identity solutions. This includes Hyperledger Indy, a suite of tools for creating a system of digital identities stored on blockchains and distributed ledgers. Sovrin is a popular decentralized identity management solution built using Hyperledger Indy.
Decentralized Identity Foundation
 Source: Identity.foundation
Source: Identity.foundation
The Decentralized Identity Foundation (DIF) is committed to creating an interoperable system for decentralized identities. For years, lack of interoperability has been a stumbling block for the mass adoption of decentralized identities.
The DIF is working closely with key players to achieve cross-platform use of DID frameworks. This will allow users to use their digital identities across a world of apps, devices, and services.
Notable DIF members include Microsoft, Evernym, Sovrin, IBM, Hyperledger, Blockstack, and Enterprise Ethereum Alliance.
Final Thoughts
Decentralized identity can change how we think of personal information and user data in the 21st century. With DIDs and VCs, users can regain control of their identities, instead of trusting Big Tech companies to safeguard sensitive information.
Decentralized identity has revolutionary benefits for businesses, too. They can eliminate burdensome identity verification and provide seamless and secure online experiences for users. And by committing to protecting user information, organizations can build trust and enjoy better relationships with customers.
To learn more about web3, NFTs, and the blockchain, check out Hashnode’s web3 blog

